Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Last updated 20 setembro 2024

Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store

Banking Trojans sneaked into Google Play store disguised as apps

DLLSpy – Tighten Your Defense by Discovering DLL Hijacking Easily

How to Prevent Dynamic Hooking of Android Apps

Analysis of dynamic code updating in Android with security

Analysis of dynamic code updating in Android with security

Android: With Android 14, Google has a new plan to make your

How to Code Sign Secured Android App with SHA Fingerprint Google

Cyberattack Disrupts Hospital Computer Systems Across US, Oregon

Joker Malware Apps Once Again Bypass Google's Security to Spread
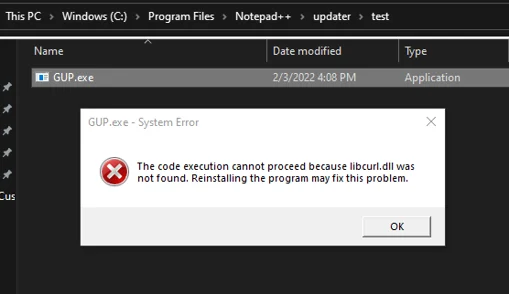
THREAT ANALYSIS REPORT: DLL Side-Loading Widely (Ab)Used

Analysis of dynamic code updating in Android with security

Android App Disguised as a QR scanner, Spreads Joker Variant Trojan
Recomendado para você
-
 Roblox music codes, The best song IDs to use20 setembro 2024
Roblox music codes, The best song IDs to use20 setembro 2024 -
 Evade Codes (December 2023) - Roblox20 setembro 2024
Evade Codes (December 2023) - Roblox20 setembro 2024 -
Codes, Roblox Evade Wiki20 setembro 2024
-
 Evade 🍀 Codes Wiki 2023 - St Patricks Update Codes20 setembro 2024
Evade 🍀 Codes Wiki 2023 - St Patricks Update Codes20 setembro 2024 -
 Evolution Evade Codes - Try Hard Guides20 setembro 2024
Evolution Evade Codes - Try Hard Guides20 setembro 2024 -
 Roblox Evolution Evade Codes January 2023 in 202320 setembro 2024
Roblox Evolution Evade Codes January 2023 in 202320 setembro 2024 -
 roblox evade song ids 2023 june|TikTok Search20 setembro 2024
roblox evade song ids 2023 june|TikTok Search20 setembro 2024 -
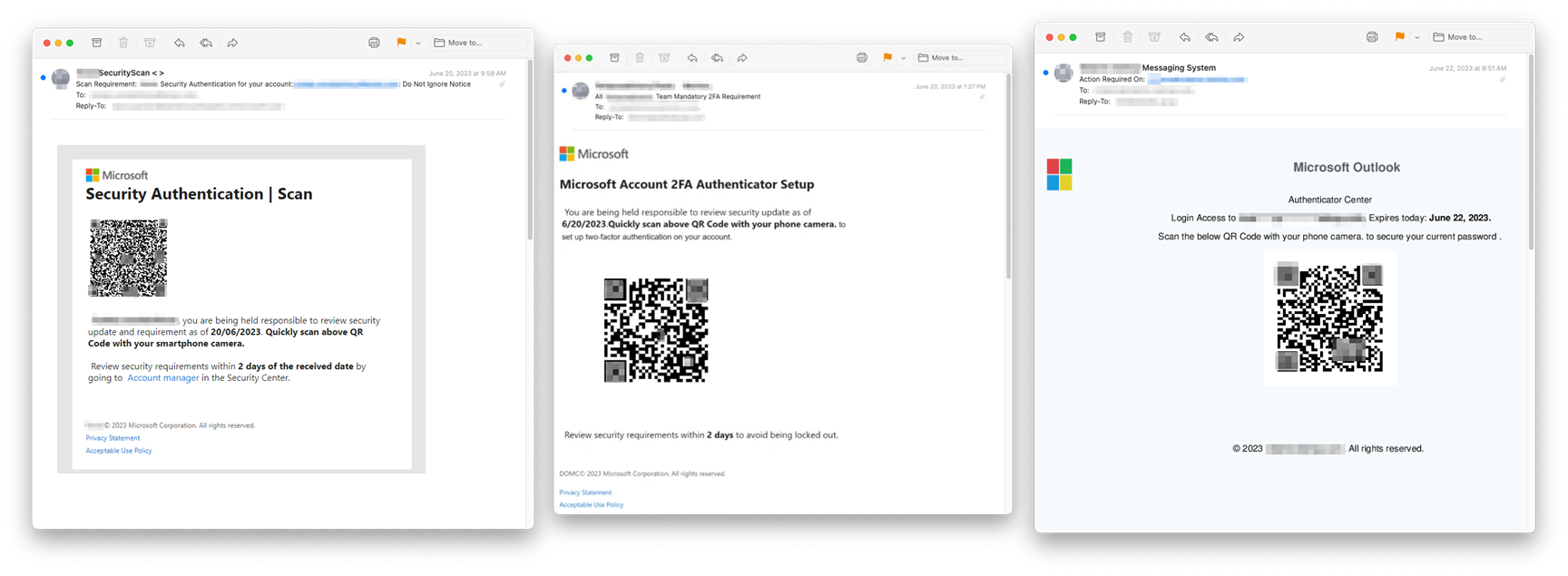 Cybercriminals are circumventing email security with image-based20 setembro 2024
Cybercriminals are circumventing email security with image-based20 setembro 2024 -
Data Encoder Crypter20 setembro 2024
-
 College Presidents Under Fire After Dodging Questions About20 setembro 2024
College Presidents Under Fire After Dodging Questions About20 setembro 2024
você pode gostar
-
 VicTycoon Art - BANNER - Mary Games20 setembro 2024
VicTycoon Art - BANNER - Mary Games20 setembro 2024 -
 GTA MTA RP - COMO COMEÇAR NO DESTINY RP (ATUALIZADO) Five M de Pobre20 setembro 2024
GTA MTA RP - COMO COMEÇAR NO DESTINY RP (ATUALIZADO) Five M de Pobre20 setembro 2024 -
 European basketball league hi-res stock photography and images20 setembro 2024
European basketball league hi-res stock photography and images20 setembro 2024 -
 ESL Games and Game Board20 setembro 2024
ESL Games and Game Board20 setembro 2024 -
One Piece Special Edition (HD, Subtitled): Alabasta (62-135) Ace and Luffy! Hot Emotions and Brotherly Bonds! - Watch on Crunchyroll20 setembro 2024
-
![OC] Zoro in Asura Yoru mode : r/OnePiece](https://preview.redd.it/zoro-in-asura-yoru-mode-v0-vnj29eahysb91.jpg?width=1836&format=pjpg&auto=webp&s=46d8c9b6131ec247ca93b2b9c32e57ad12929309) OC] Zoro in Asura Yoru mode : r/OnePiece20 setembro 2024
OC] Zoro in Asura Yoru mode : r/OnePiece20 setembro 2024 -
단기 매매 종목 추천 사이트(방문:CXAIG.com)jRoX em Promoção na Shopee Brasil 202320 setembro 2024
-
 WrestleQuest - IGN20 setembro 2024
WrestleQuest - IGN20 setembro 2024 -
Street Fighter - QUICK! You see Blanka-Chan coming at you20 setembro 2024
-
NEW* FREE CODES GRAND PIECE ONLINE gives FREE FRUIT RESET + FREE SP RESET + FREE NOTIFIER ROBLOX #2KidsInApod #Roblox #FreeCodes #Anime #OnePiece #Gaming *NEW* FREE CODES GRAND PIECE ONLINE gives20 setembro 2024




