Cybercriminals are circumventing email security with image-based
Por um escritor misterioso
Last updated 17 dezembro 2024
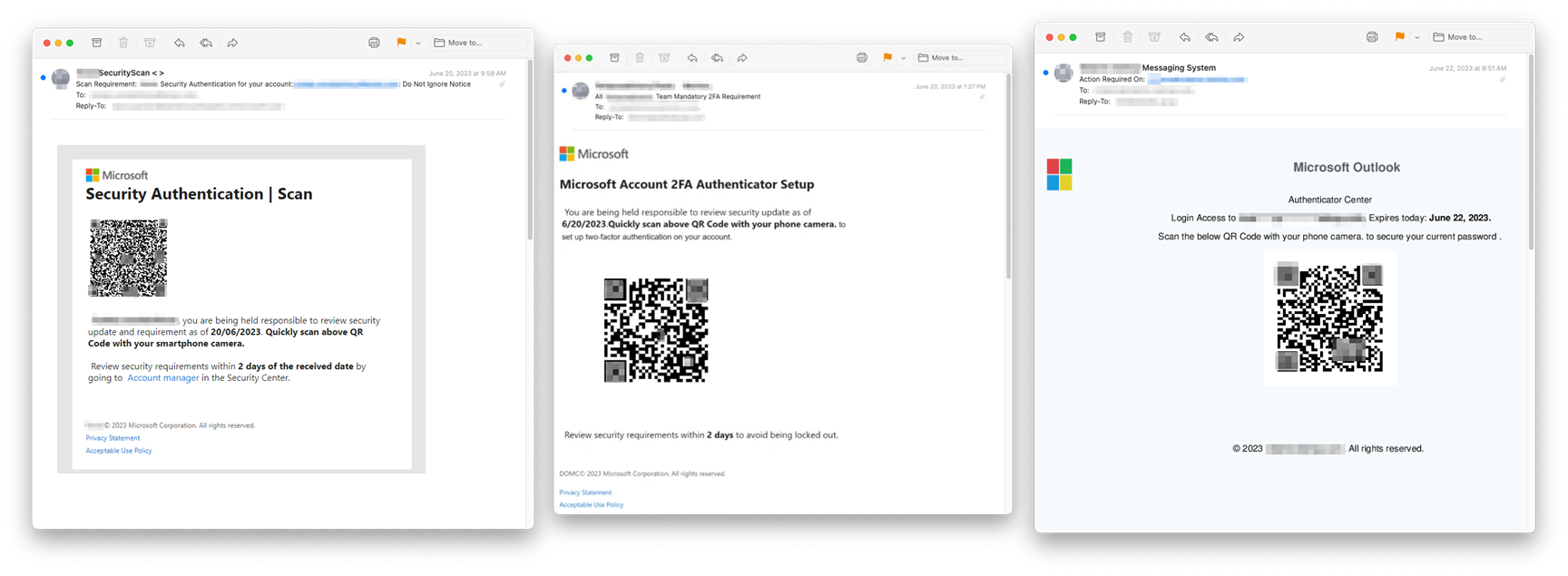
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't

How you could become a victim of cybercrime in 2015, Cybercrime

Microsoft: BEC Attackers Evade 'Impossible Travel' Flags With Residential IP Addresses

Comparing different AI approaches to email security

Cybercriminals Bypass OpenAI's Restrictions on Malicious Use

Hackers Are Bypassing Your Email Security Solution & Here's Ho - Guardian Digital .

Novel SMTP Smuggling Technique Slips Past DMARC, Email Protections

VIPRE finds 233.9 million malicious emails detected in Q3 2023

Information Security Buzz Article: Step Up Your Defense Against Cloud-loving Cybercriminals

Email Security Tech: No Guarantee of Protection from BEC - eftsure

Threat Actors Using Google AMP To Evade Phishing Attacks

Cybercriminals Can Use ChatGPT to Their Advantage

4 best email security tools you need in your stack
_11zon.jpg)
Darktrace/Email in Action: Why AI-Driven Email Security is the Best Defense Against Sustained Phishing Campaigns

The 10 Worst Cyber Crimes Analysed

Understanding Phishing Emails: Why They Slip Through Spam Filters
Recomendado para você
-
 Roblox Evade Codes (November 2023)17 dezembro 2024
Roblox Evade Codes (November 2023)17 dezembro 2024 -
 Roblox: Evade Codes17 dezembro 2024
Roblox: Evade Codes17 dezembro 2024 -
 Roblox Baby Simulator Codes (November 2023)17 dezembro 2024
Roblox Baby Simulator Codes (November 2023)17 dezembro 2024 -
![Evade My New Favorite Game - Roblox [EN - ES]🎮👾](https://images.hive.blog/1200x630/https://files.peakd.com/file/peakd-hive/wuildariablox/23tbiSXPvXM1RFAxtNJLYiYiPv3grTM1tTmmMMFbjoqDM5draL1DQF8ubSsfCA4QCVfsA.png) Evade My New Favorite Game - Roblox [EN - ES]🎮👾17 dezembro 2024
Evade My New Favorite Game - Roblox [EN - ES]🎮👾17 dezembro 2024 -
 Evade Codes (Roblox) in 2023 Coding, Roblox, Roblox codes17 dezembro 2024
Evade Codes (Roblox) in 2023 Coding, Roblox, Roblox codes17 dezembro 2024 -
 Roblox Evade Codes (June 2023): Free Customization17 dezembro 2024
Roblox Evade Codes (June 2023): Free Customization17 dezembro 2024 -
 CODES – Evade! - Rick News17 dezembro 2024
CODES – Evade! - Rick News17 dezembro 2024 -
 NEW* ALL WORKING CODES FOR EVADE IN MARCH 2023! ROBLOX EVADE CODES17 dezembro 2024
NEW* ALL WORKING CODES FOR EVADE IN MARCH 2023! ROBLOX EVADE CODES17 dezembro 2024 -
 Roblox Evolution Evade Codes January 2023 in 202317 dezembro 2024
Roblox Evolution Evade Codes January 2023 in 202317 dezembro 2024 -
 Attackers use dynamic code loading to bypass Google Play store's17 dezembro 2024
Attackers use dynamic code loading to bypass Google Play store's17 dezembro 2024
você pode gostar
-
 Prisoner Astraytale Sans - Sans Undertale Minecraft Pixel Art17 dezembro 2024
Prisoner Astraytale Sans - Sans Undertale Minecraft Pixel Art17 dezembro 2024 -
 EB letter logo. Unique attractive creative modern initial BE EB or E B initial based letter icon logo 5425025 Vector Art at Vecteezy17 dezembro 2024
EB letter logo. Unique attractive creative modern initial BE EB or E B initial based letter icon logo 5425025 Vector Art at Vecteezy17 dezembro 2024 -
 NUOTI Anime Hitori No Shita Poster Under One Person Poster Poster Decorative Painting Canvas Wall Art Living Room Posters Bedroom Painting 12x18inch(30x45cm) : לבית ולמטבח17 dezembro 2024
NUOTI Anime Hitori No Shita Poster Under One Person Poster Poster Decorative Painting Canvas Wall Art Living Room Posters Bedroom Painting 12x18inch(30x45cm) : לבית ולמטבח17 dezembro 2024 -
 Counter-Strike: Condition Zero (Gearbox Software design)17 dezembro 2024
Counter-Strike: Condition Zero (Gearbox Software design)17 dezembro 2024 -
 Jogo de xadrez com peças formadas por roupas de vidro e metal17 dezembro 2024
Jogo de xadrez com peças formadas por roupas de vidro e metal17 dezembro 2024 -
 More New Brazilian Character Posters for DC LEAGUE OF SUPER-PETS : r/DCEUleaks17 dezembro 2024
More New Brazilian Character Posters for DC LEAGUE OF SUPER-PETS : r/DCEUleaks17 dezembro 2024 -
assets./image/upload/ar_16:9,b_auto:bo17 dezembro 2024
-
 Smash Mouth Vocalist Steve Harwell Dies Aged 5617 dezembro 2024
Smash Mouth Vocalist Steve Harwell Dies Aged 5617 dezembro 2024 -
 CapCut_daddy's issues the neighborhood concert17 dezembro 2024
CapCut_daddy's issues the neighborhood concert17 dezembro 2024 -
 Guia da Copa do Mundo 2022: Tabela com todos os jogos, dias, horários e onde assistir – Money Times17 dezembro 2024
Guia da Copa do Mundo 2022: Tabela com todos os jogos, dias, horários e onde assistir – Money Times17 dezembro 2024
