Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 21 setembro 2024

Describing activities of a crime group attacking Ukraine.
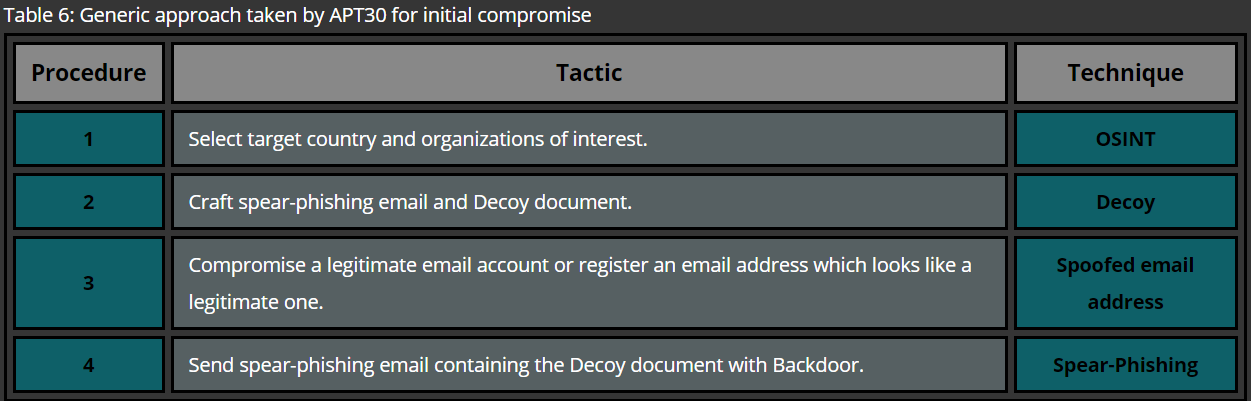
Initial Compromise

Initial access brokers: How are IABs related to the rise in ransomware attacks?

You could be hacked and not know it - Storcom, Lombard, Illinois, United States of America
Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

System model of attribute-based access control for proxy re-encryption

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Initial Access Brokers - who are they, what do they do, and how can you protect yourself?

Initial access broker repurposing techniques in targeted attacks against Ukraine
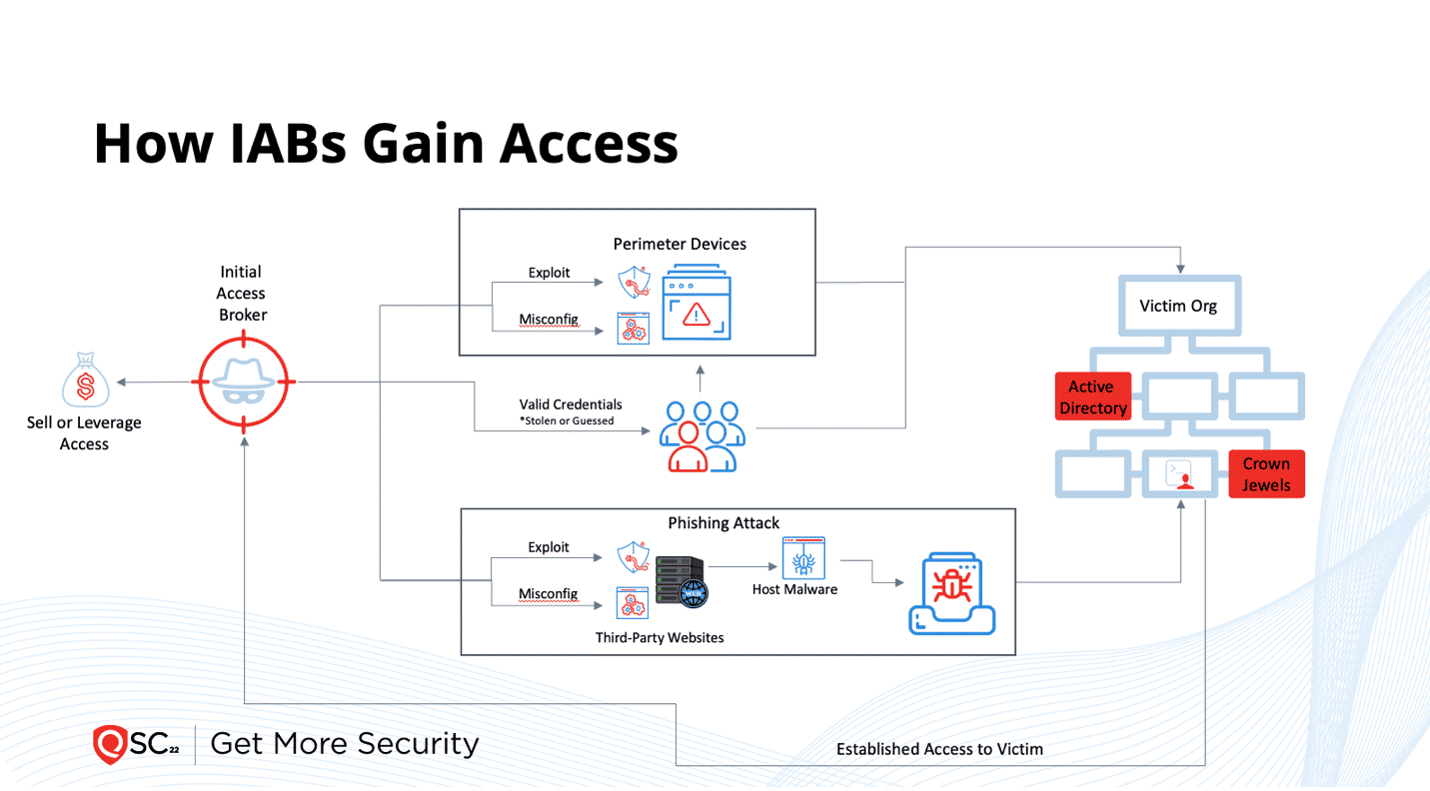
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore

Security in product lifecycle of IoT devices: A survey - ScienceDirect

US20080120240A1 - Trusted infrastructure support systems, methods and techniques for secure electronic commerce, electronic transactions, commerce process control and automation, distributed computing, and rights management - Google Patents

Transfer Learning: Repurposing ML Algorithms from Different Domains to Cloud Defense

Targeted Cyberattacks: A Superset of Advanced Persistent Threats
Recomendado para você
-
 Analysis Group New York21 setembro 2024
Analysis Group New York21 setembro 2024 -
Analysis Group HealthEconomics.com Jobs Portal21 setembro 2024
-
 Analysis Group - P&R Desjardins21 setembro 2024
Analysis Group - P&R Desjardins21 setembro 2024 -
 Analysis Group Office Photos21 setembro 2024
Analysis Group Office Photos21 setembro 2024 -
 Administrative Staff - Analysis Group21 setembro 2024
Administrative Staff - Analysis Group21 setembro 2024 -
 Prigozhin interests and Russian information operations21 setembro 2024
Prigozhin interests and Russian information operations21 setembro 2024 -
 IAG Strategic Imaging for Accelerated Drug Development21 setembro 2024
IAG Strategic Imaging for Accelerated Drug Development21 setembro 2024 -
 Job Listings at Analysis Group, Inc.21 setembro 2024
Job Listings at Analysis Group, Inc.21 setembro 2024 -
 Media Ecosystems Analysis Group21 setembro 2024
Media Ecosystems Analysis Group21 setembro 2024 -
 USC/AG Antitrust and Competition Event21 setembro 2024
USC/AG Antitrust and Competition Event21 setembro 2024
você pode gostar
-
 Twist After Twist After Twist ! Tomodachi Game Episode 10 Reaction ! Tomodachi game Anime Reaction21 setembro 2024
Twist After Twist After Twist ! Tomodachi Game Episode 10 Reaction ! Tomodachi game Anime Reaction21 setembro 2024 -
 EA Sports FC 24 Review: Gameplay, Ultimate Team and Career Mode Impressions, Videos, News, Scores, Highlights, Stats, and Rumors21 setembro 2024
EA Sports FC 24 Review: Gameplay, Ultimate Team and Career Mode Impressions, Videos, News, Scores, Highlights, Stats, and Rumors21 setembro 2024 -
 Minas Tênis Clube - Minas Náutico21 setembro 2024
Minas Tênis Clube - Minas Náutico21 setembro 2024 -
 🎃 INFERNAL UPDATE 🎃 FIRE FORCE ONLINE CODES - CODES FOR ROBLOX21 setembro 2024
🎃 INFERNAL UPDATE 🎃 FIRE FORCE ONLINE CODES - CODES FOR ROBLOX21 setembro 2024 -
 Arquivos21 setembro 2024
Arquivos21 setembro 2024 -
 Quem você seria em Nanatsu no Taizai21 setembro 2024
Quem você seria em Nanatsu no Taizai21 setembro 2024 -
 Fit fierce fabulous svg cut file for silhouette cricut and21 setembro 2024
Fit fierce fabulous svg cut file for silhouette cricut and21 setembro 2024 -
GitHub - meitswami/IP-Grabber: This small PHP, JS, HTML Script grabs the IP of the victim and creates a log of the IP's on the server after the Link is open by the21 setembro 2024
-
 Cross Road Blues (Crossroads)" Sheet Music by Eric Clapton; Robert Johnson; Cream for Easy Guitar Tab - Sheet Music Now21 setembro 2024
Cross Road Blues (Crossroads)" Sheet Music by Eric Clapton; Robert Johnson; Cream for Easy Guitar Tab - Sheet Music Now21 setembro 2024 -
 B: The Beginning Artworks Art Book21 setembro 2024
B: The Beginning Artworks Art Book21 setembro 2024