11 Types of Spoofing Attacks Every Security Professional Should
Por um escritor misterioso
Last updated 04 outubro 2024

The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. The goal is to feign trust, gain a foothold in a system, get hold of data, pilfer money, or distribute predatory software. What can black hats try to . . .
The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. Out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days.

Network Protocols for Security Professionals
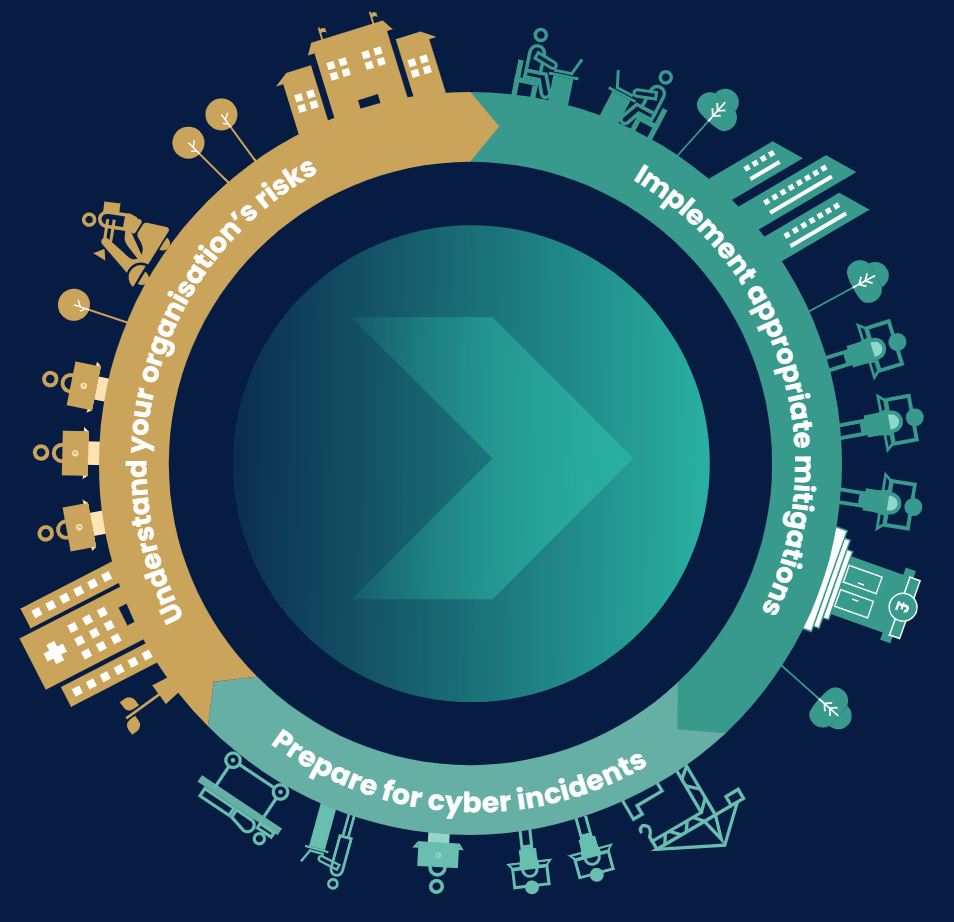
10 Steps to Cyber Security
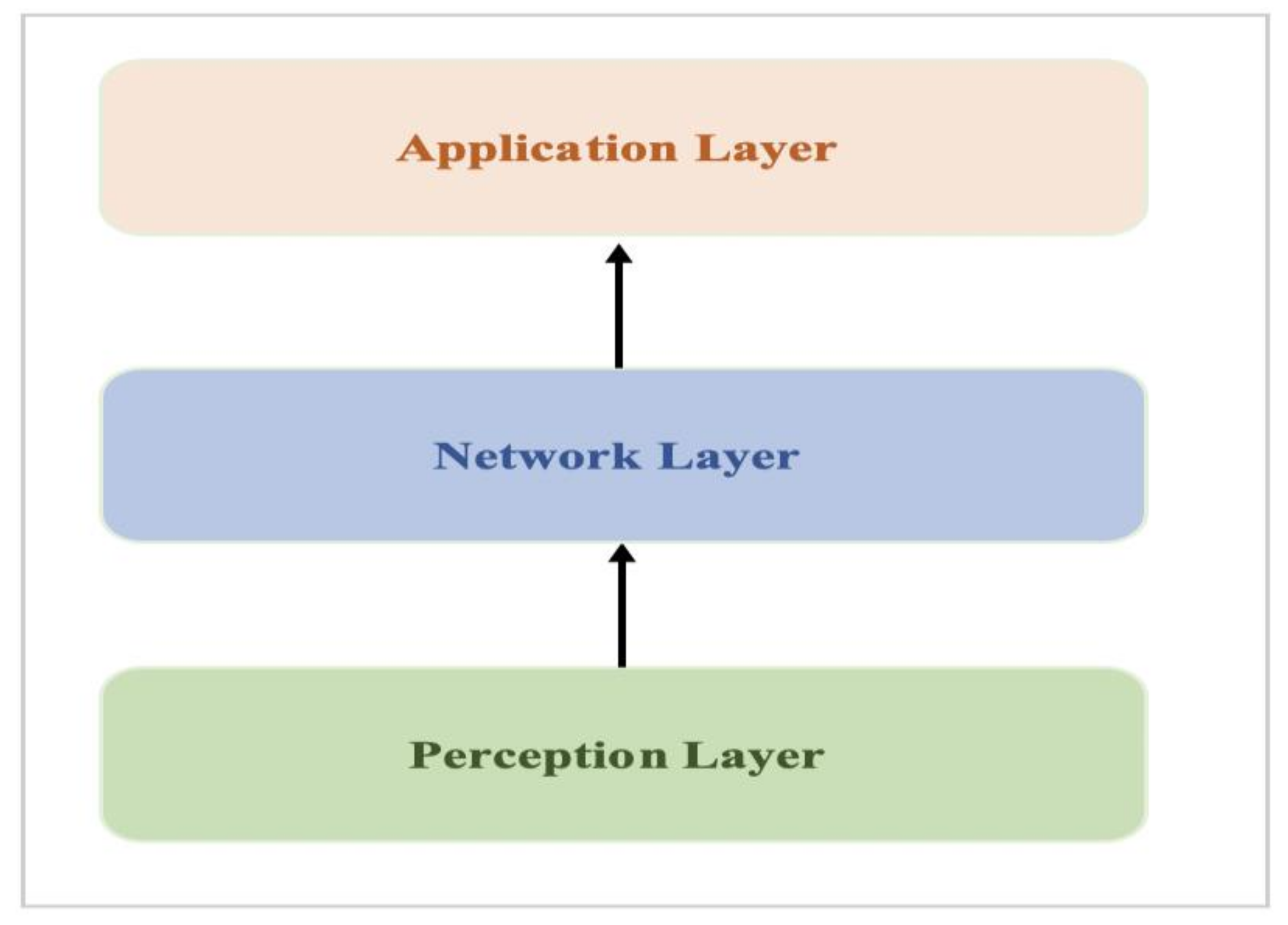
Electronics, Free Full-Text
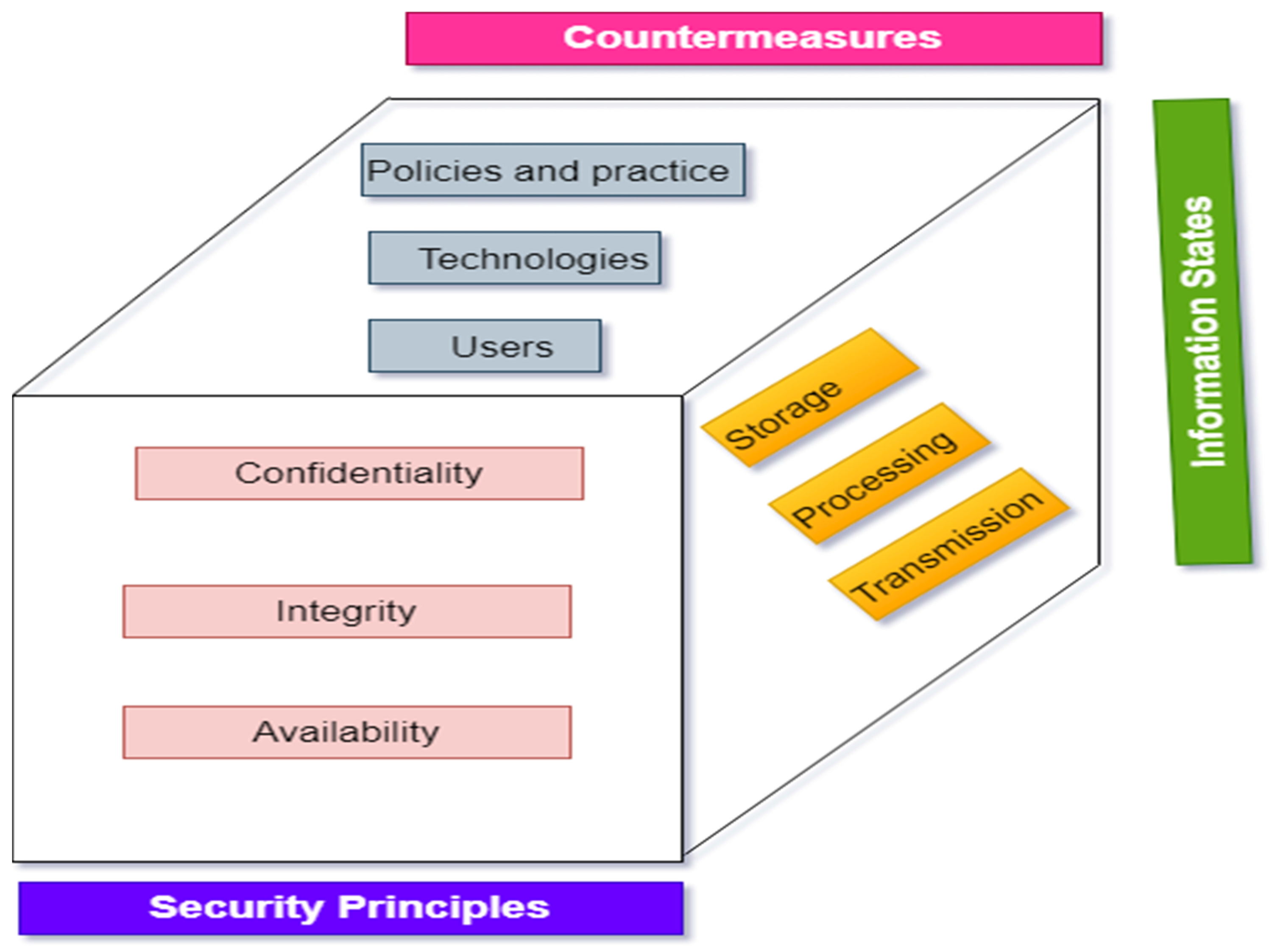
Electronics, Free Full-Text

Must Know Phishing Statistics In 2023 - Attacks And Breaches

What is Spoofing?, Examples & Prevention

Most Common Types of Cyber Attacks on Small Businesses

KnowBe4 Report Finds More Users Are Falling for Security and HR
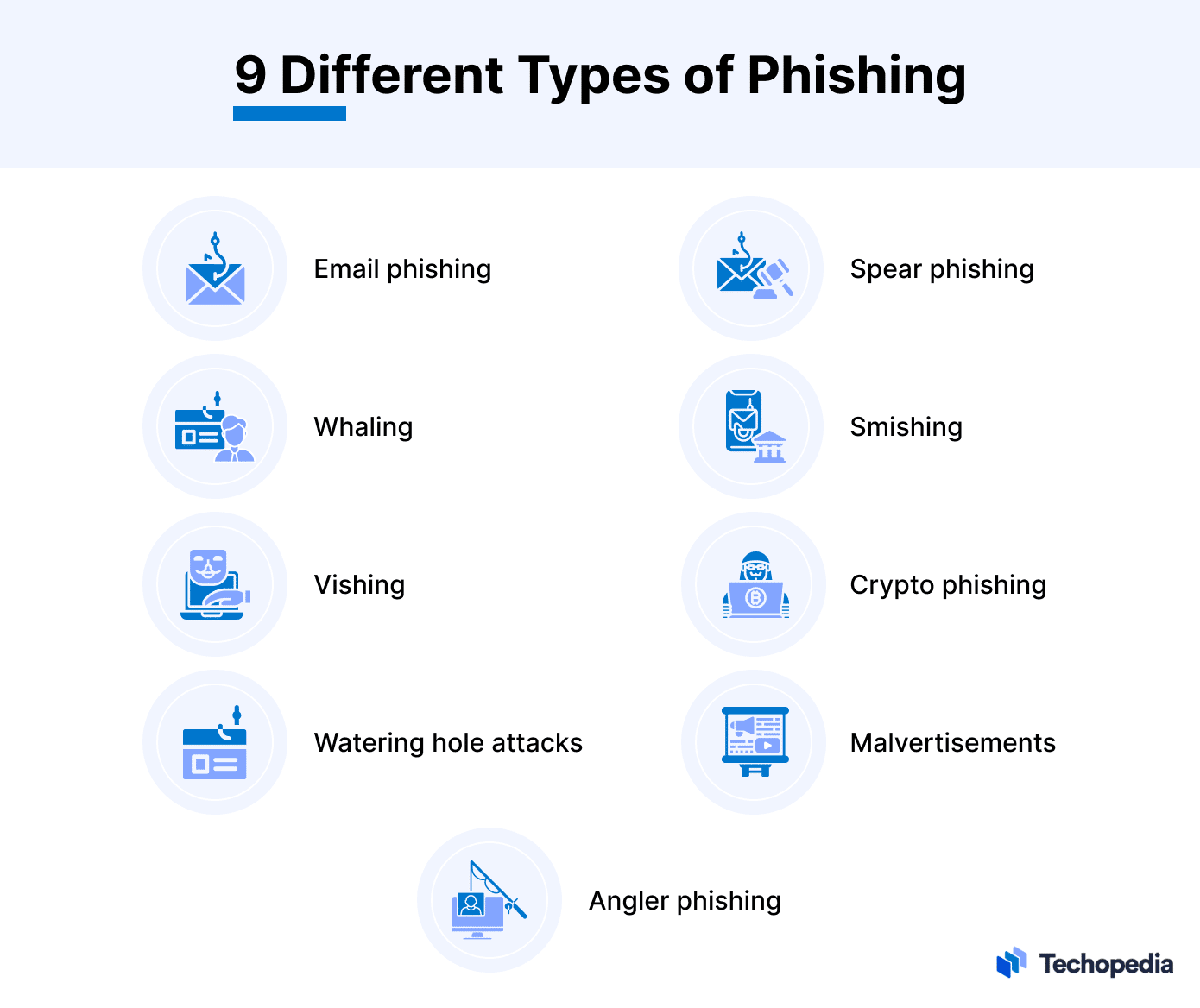
What is Phishing? - Definition With Examples From Techopedia
Recomendado para você
-
GitHub - SonsoFsERpent/redEngine-Spoofer: With the redENGINE04 outubro 2024
-
 meu cachorro morreu e agora não tenho dinheiro para spoofer no04 outubro 2024
meu cachorro morreu e agora não tenho dinheiro para spoofer no04 outubro 2024 -
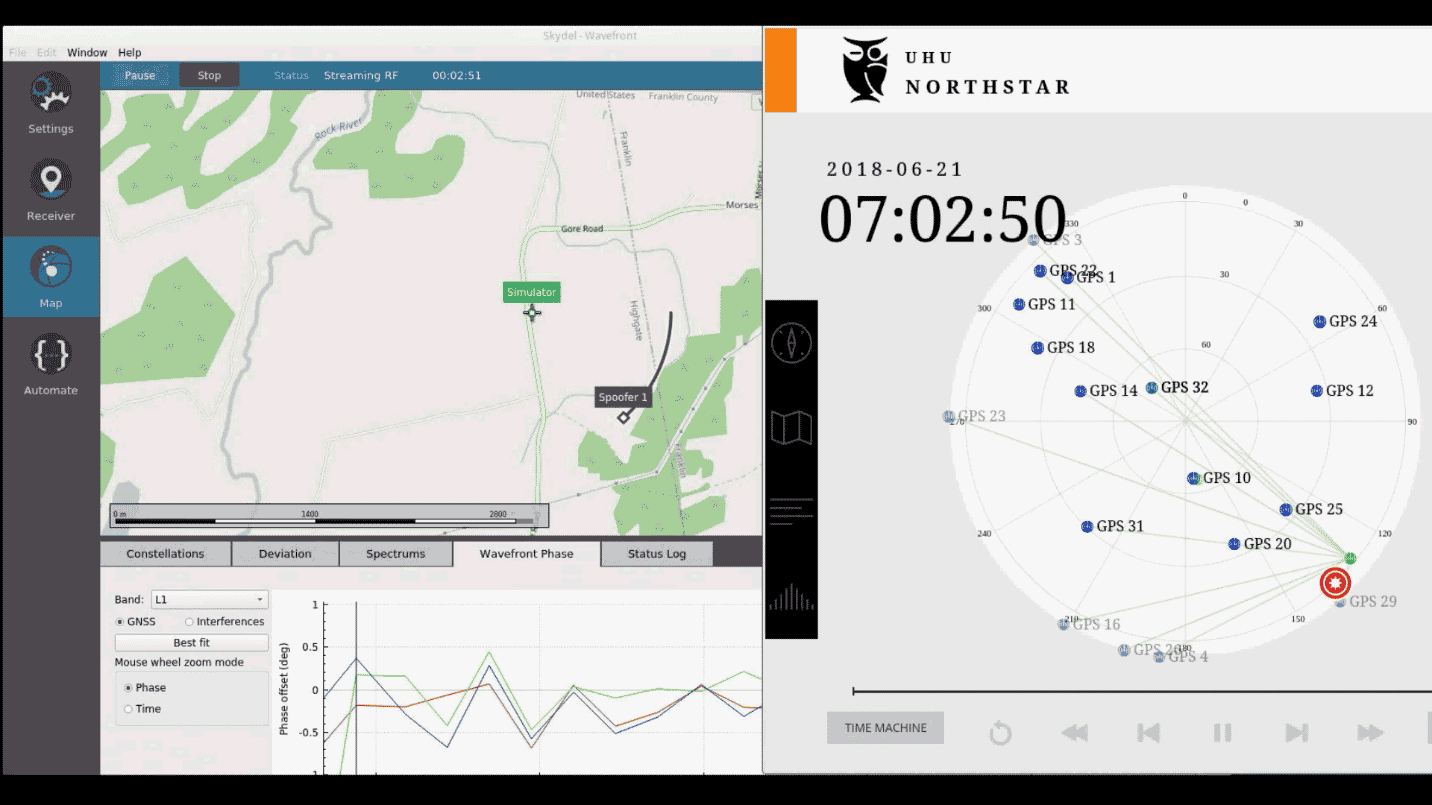 An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing04 outubro 2024
An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing04 outubro 2024 -
 Spoofers Revealed04 outubro 2024
Spoofers Revealed04 outubro 2024 -
 SimGEN Simulator and PNT Product Improvements - Spirent04 outubro 2024
SimGEN Simulator and PNT Product Improvements - Spirent04 outubro 2024 -
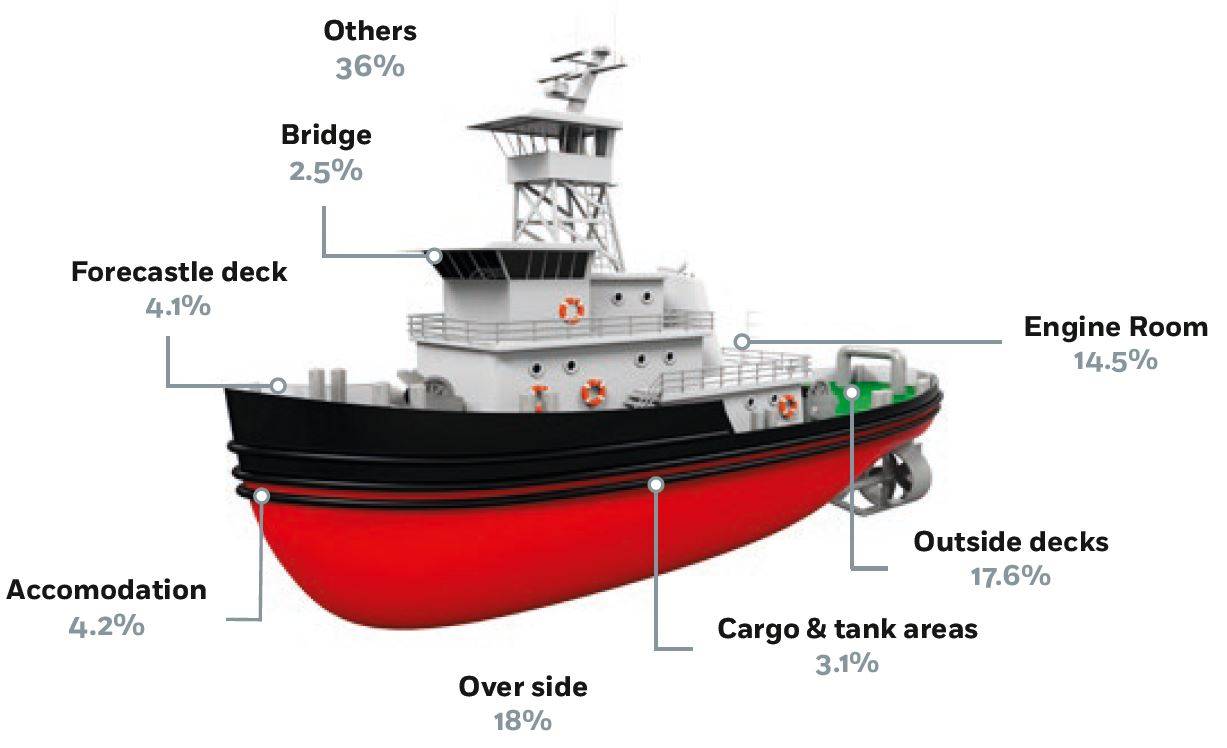 Autonomous Shipping – Cyber Hazards Ahead04 outubro 2024
Autonomous Shipping – Cyber Hazards Ahead04 outubro 2024 -
 Off-Road Racebikes—Ty Cullins' 2022 TM EN 30004 outubro 2024
Off-Road Racebikes—Ty Cullins' 2022 TM EN 30004 outubro 2024 -
 Fortune India: Business News, Strategy, Finance and Corporate Insight04 outubro 2024
Fortune India: Business News, Strategy, Finance and Corporate Insight04 outubro 2024 -
 Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools04 outubro 2024
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools04 outubro 2024 -
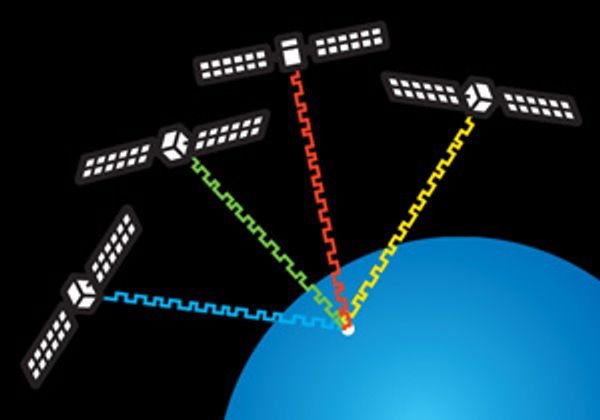 Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum04 outubro 2024
Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum04 outubro 2024
você pode gostar
-
 Cuba - Cuba - Results, fixtures, squad, statistics, photos, videos04 outubro 2024
Cuba - Cuba - Results, fixtures, squad, statistics, photos, videos04 outubro 2024 -
 How to login Roblox, Roblox Login 202304 outubro 2024
How to login Roblox, Roblox Login 202304 outubro 2024 -
 😢Melhores vídeos tristes😢 para status de Whatsapp04 outubro 2024
😢Melhores vídeos tristes😢 para status de Whatsapp04 outubro 2024 -
 MASH IS BAD ASS!!! Mashle Magic & Muscles Episode 1 Reaction04 outubro 2024
MASH IS BAD ASS!!! Mashle Magic & Muscles Episode 1 Reaction04 outubro 2024 -
 Peça de xadrez Livro para colorir Desenho Peão, xadrez, jogo, esportes, tabuleiro Jogo png04 outubro 2024
Peça de xadrez Livro para colorir Desenho Peão, xadrez, jogo, esportes, tabuleiro Jogo png04 outubro 2024 -
id de roupas no bloxburg pra look vibe|Pesquisa do TikTok04 outubro 2024
-
 Skeleton Knight in Another World Episódio 6 Data de lançamento, hora e recapitulação - BR Atsit04 outubro 2024
Skeleton Knight in Another World Episódio 6 Data de lançamento, hora e recapitulação - BR Atsit04 outubro 2024 -
 Sakata Shogo, Inoue Marina, and Fujii Yukiyo Take Part in the Lighthouse Anthropomorphize Project “Akari no Moribito” New Reading Stage at “Niconico Chokaigi 2023”04 outubro 2024
Sakata Shogo, Inoue Marina, and Fujii Yukiyo Take Part in the Lighthouse Anthropomorphize Project “Akari no Moribito” New Reading Stage at “Niconico Chokaigi 2023”04 outubro 2024 -
 Giant Chess Set – Houston Party Rental Inc. Spring TX04 outubro 2024
Giant Chess Set – Houston Party Rental Inc. Spring TX04 outubro 2024 -
 Pista Trem De Resgate Patrulha Canina - Compre Agora04 outubro 2024
Pista Trem De Resgate Patrulha Canina - Compre Agora04 outubro 2024
