Malware analysis
Por um escritor misterioso
Last updated 17 dezembro 2024

GPT's Journey into Malware Analysis - Check Point Blog
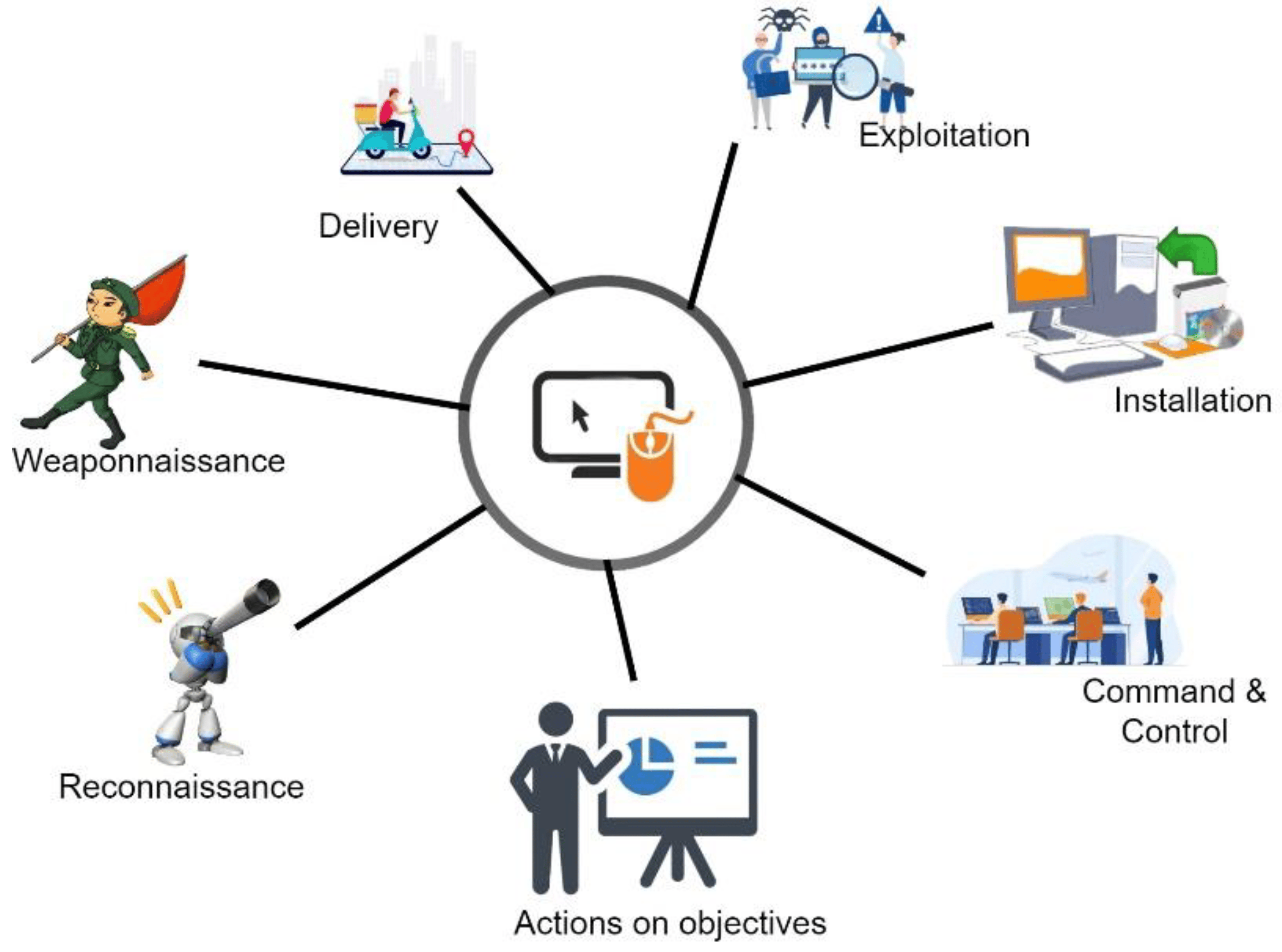
Symmetry, Free Full-Text

The different types of Malware Analysis, by Dunst Consulting

How to Do Malware Analysis?
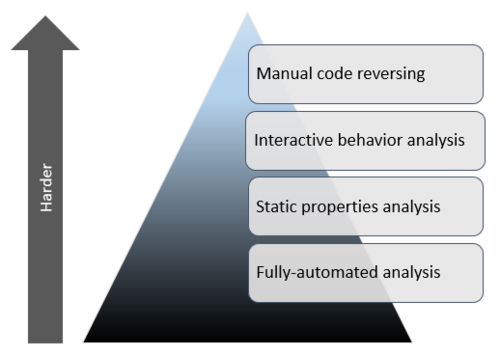
Mastering 4 Stages of Malware Analysis

TryHackMe Malware Analysis

Malware Analysis: Steps & Examples - CrowdStrike

Recorded Future closes acquisition of malware analysis firm

Malware Analysis Fundamentals

Malware Analysis - Credly
Master Reverse Engineering, Malware Analysis, Linux, Cyber Security, Ghidra,x86-64, IDA Pro, IDA Free, Assembly and NASM

Mastering Reverse Engineering & Malware Analysis | REMASM+
Malware Analysis 4 Vital Stages of Malware Analysis You Should Know
Malware Detection in Executables Using Neural Networks
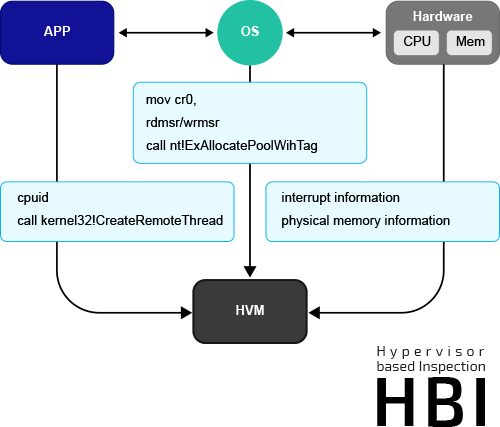
Deep Malware Analysis - Joe Sandbox Technology
Recomendado para você
-
 Stream by SagEmXne17 dezembro 2024
Stream by SagEmXne17 dezembro 2024 -
 Go To This Link - - in the comments17 dezembro 2024
Go To This Link - - in the comments17 dezembro 2024 -
 Proposal to Enhance Security Against Hyperlink Phishing Scams – Discord17 dezembro 2024
Proposal to Enhance Security Against Hyperlink Phishing Scams – Discord17 dezembro 2024 -
 www..com/watch?v=dQw4w9WgXcQ : r/Breath_of_the_Wild17 dezembro 2024
www..com/watch?v=dQw4w9WgXcQ : r/Breath_of_the_Wild17 dezembro 2024 -
 r/meme17 dezembro 2024
r/meme17 dezembro 2024 -
 r/dankmemes17 dezembro 2024
r/dankmemes17 dezembro 2024 -
 Twitch17 dezembro 2024
Twitch17 dezembro 2024 -
 dont you dare - Imgflip17 dezembro 2024
dont you dare - Imgflip17 dezembro 2024 -
Rick Rolled17 dezembro 2024
-
 Imgflip17 dezembro 2024
Imgflip17 dezembro 2024
você pode gostar
-
 Alexstrasza Standard Q Build Alexstrasza17 dezembro 2024
Alexstrasza Standard Q Build Alexstrasza17 dezembro 2024 -
Signature Care Menstrual Relief Acetaminophen 500mg Extra Strength Caplet - 40 Count - Jewel-Osco17 dezembro 2024
-
 Skip to Loafer Vol.10 Ch.56 Page 26 - Mangago17 dezembro 2024
Skip to Loafer Vol.10 Ch.56 Page 26 - Mangago17 dezembro 2024 -
 What Is The Most Powerful Piece In Chess? – Maroon Chess17 dezembro 2024
What Is The Most Powerful Piece In Chess? – Maroon Chess17 dezembro 2024 -
 Papel de Parede Xadrez LD0417 dezembro 2024
Papel de Parede Xadrez LD0417 dezembro 2024 -
 Pinball FX3 - Star Wars™ Pinball: The Last Jedi™ on Steam17 dezembro 2024
Pinball FX3 - Star Wars™ Pinball: The Last Jedi™ on Steam17 dezembro 2024 -
 Blue Protocol Brasil (@BlueProtocolBR) / X17 dezembro 2024
Blue Protocol Brasil (@BlueProtocolBR) / X17 dezembro 2024 -
 Japan's Making A Live-Action Fullmetal Alchemist Movie All Of A Sudden17 dezembro 2024
Japan's Making A Live-Action Fullmetal Alchemist Movie All Of A Sudden17 dezembro 2024 -
 Where to Watch Call of the Night: Crunchyroll, Netflix, HIDIVE in17 dezembro 2024
Where to Watch Call of the Night: Crunchyroll, Netflix, HIDIVE in17 dezembro 2024 -
 Farming Simulator MercadoLivre 📦17 dezembro 2024
Farming Simulator MercadoLivre 📦17 dezembro 2024

