How Do MAC Spoofing Attacks Work?
Por um escritor misterioso
Last updated 20 setembro 2024

In this blog, we will go into the complexities of MAC spoofing, analyzing its repercussions and emphasizing the importance of having strong security policies in place.

Attacker Spoofing Mac Address

Mastering MAC Spoofing: A Comprehensive Guide for Windows 10 and Linux
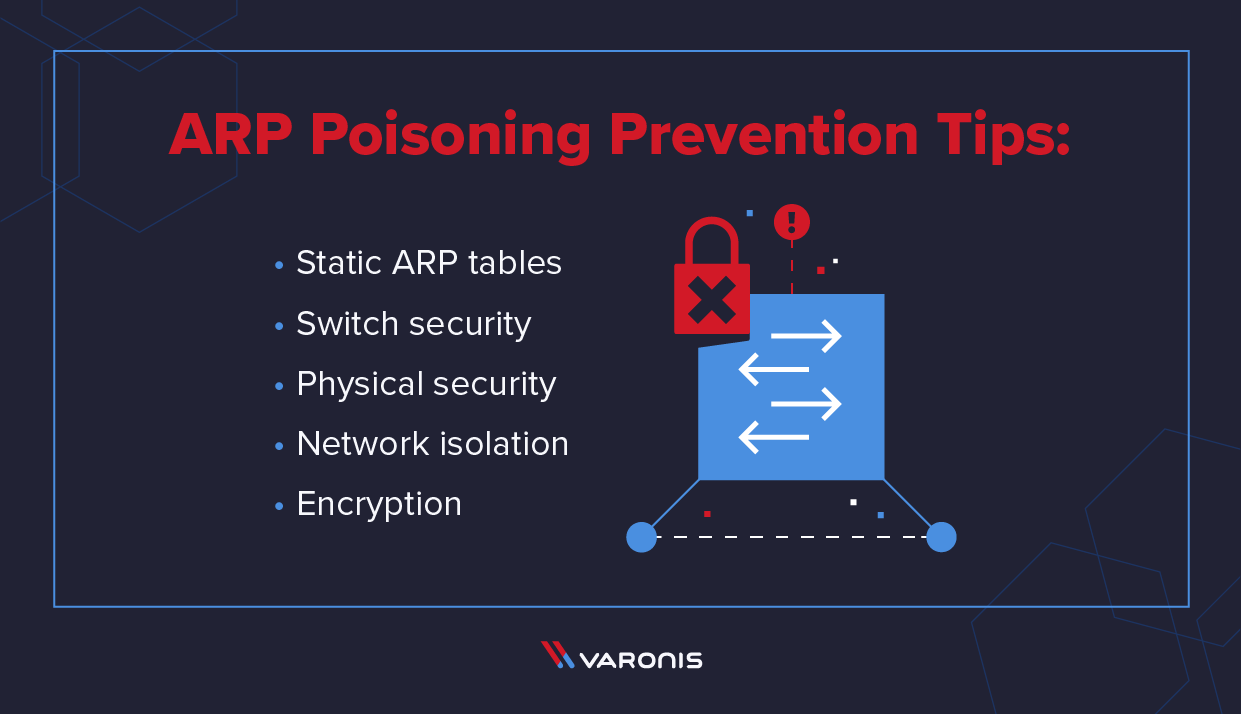
ARP Poisoning: What it is & How to Prevent ARP Spoofing Attacks

Switch Mac Basis. Switch Mac Address Table Basis
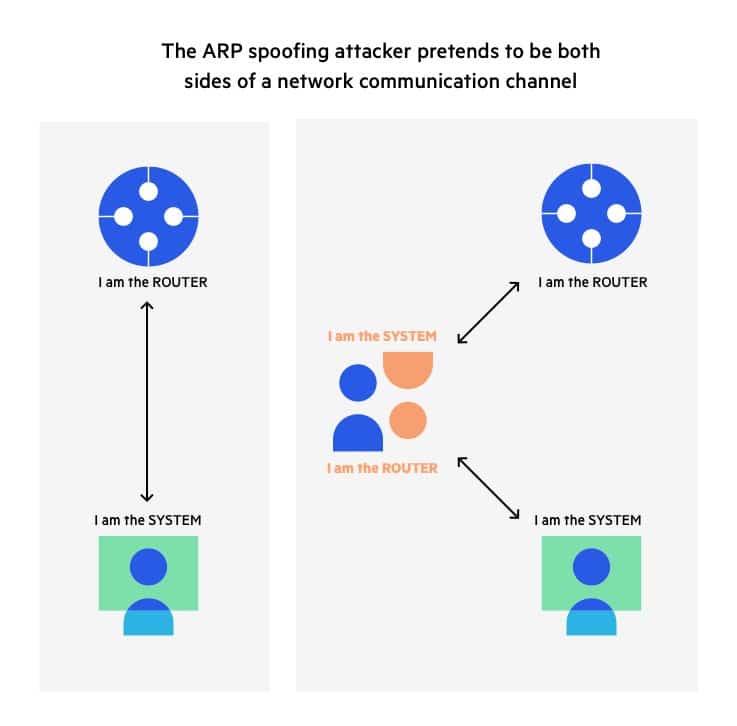
What is ARP Spoofing, ARP Cache Poisoning Attack Explained

MAC Flooding Attack - InfosecTrain
The Truth About MAC Spoofing - Portnox

What is Spoofing?, Examples & Prevention
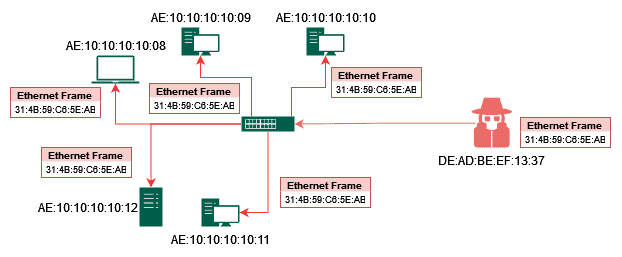
How MAC Flooding and Cloning Attacks Work?
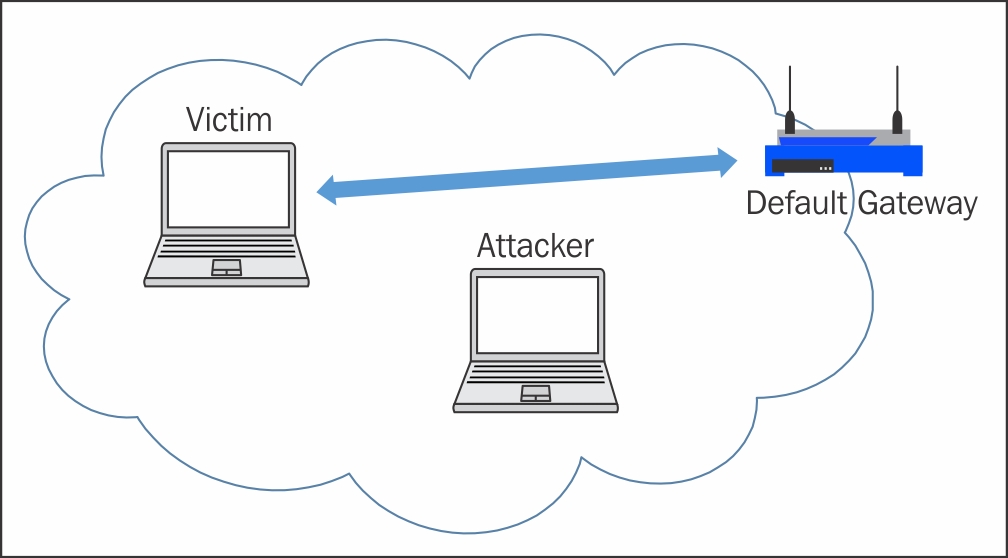
Mastering Kali Linux Wireless Pentesting
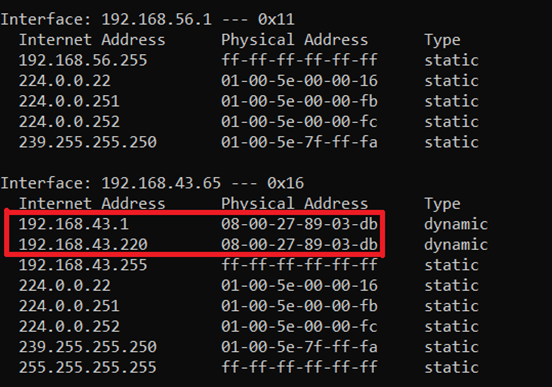
Everything You Need to Know About ARP Spoofing - Hashed Out by The SSL Store™
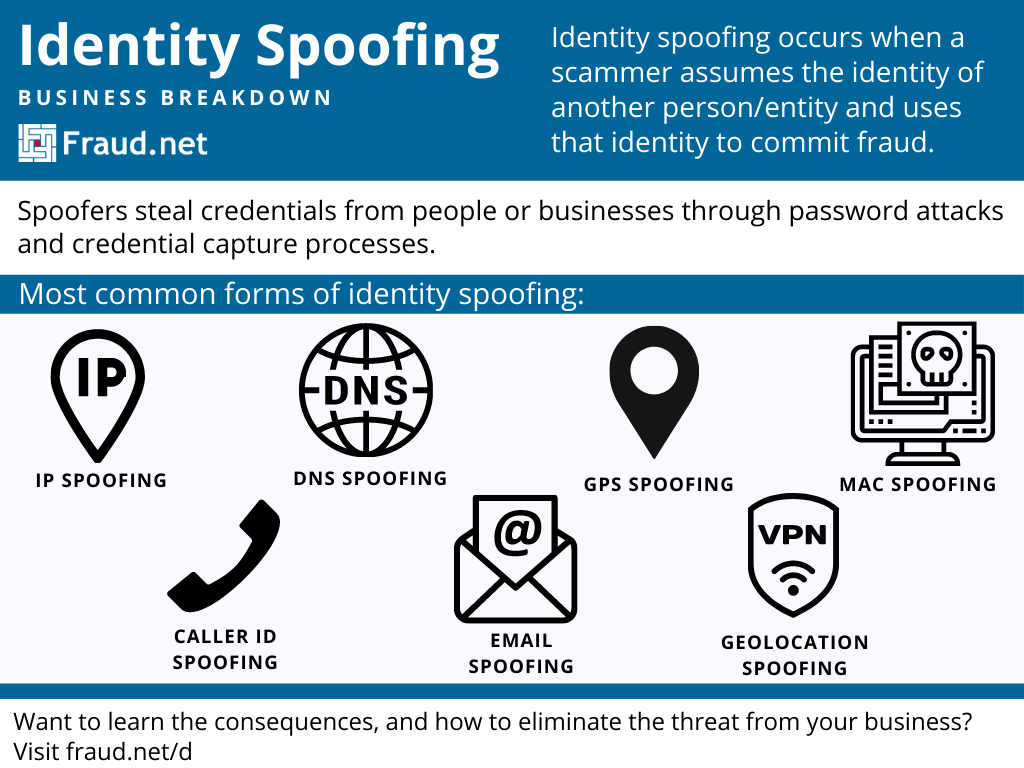
Identity Spoofing Meaning - Fraud Definitions
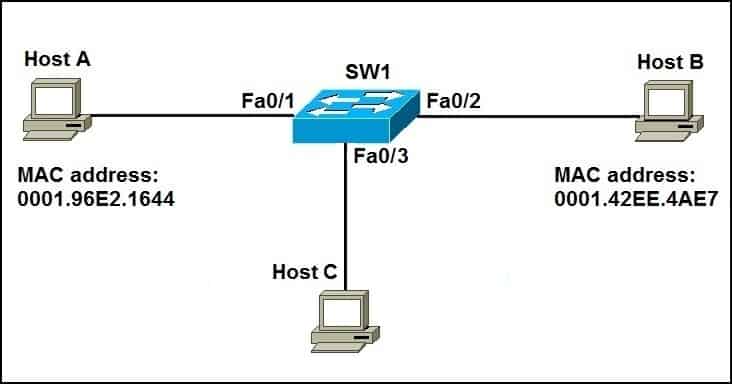
How Switches Work - Study CCNA
Recomendado para você
-
 Risk Intelligence & Device Fingerprinting Solution20 setembro 2024
Risk Intelligence & Device Fingerprinting Solution20 setembro 2024 -
 A comprehensive survey on radio frequency (RF) fingerprinting20 setembro 2024
A comprehensive survey on radio frequency (RF) fingerprinting20 setembro 2024 -
RoDAR the Equaliser20 setembro 2024
-
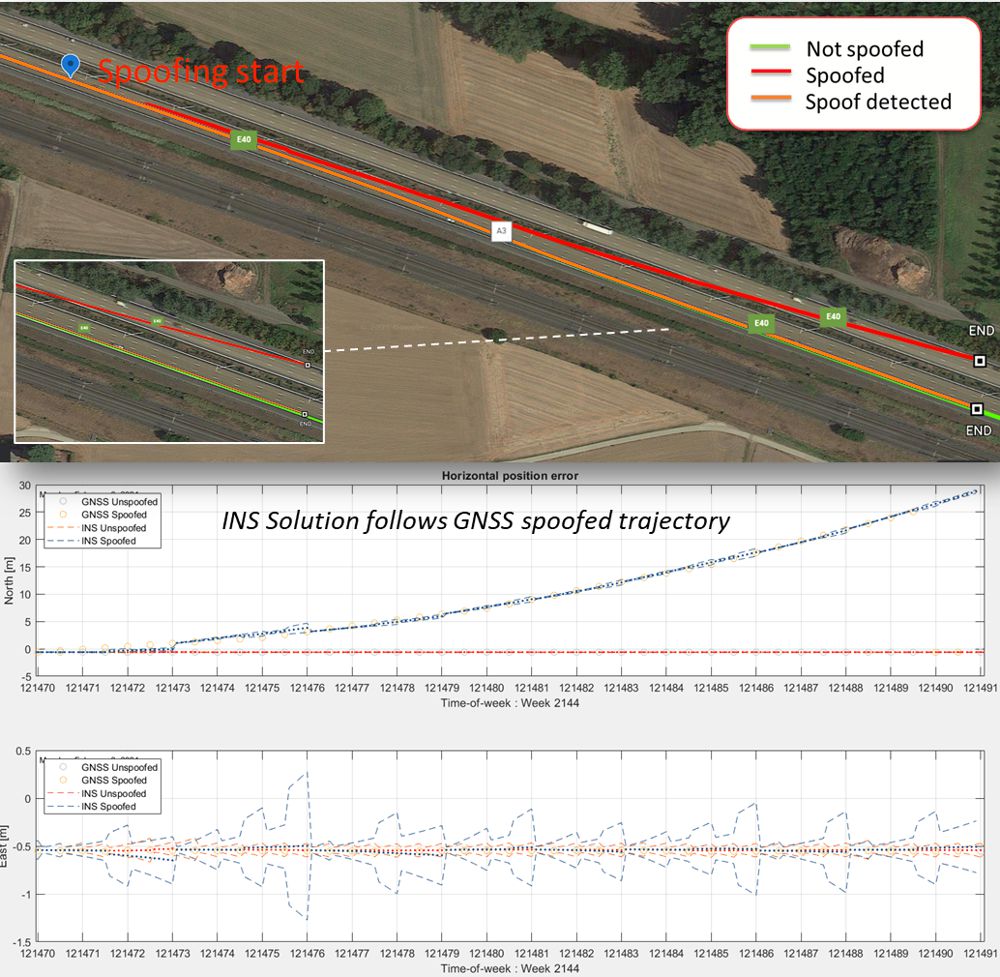 Secure GPS receivers are crucial for GNSS/INS systems - Highways Today20 setembro 2024
Secure GPS receivers are crucial for GNSS/INS systems - Highways Today20 setembro 2024 -
![Release] Spoofer](https://imgur.com/7tgB7vv.png) Release] Spoofer20 setembro 2024
Release] Spoofer20 setembro 2024 -
 Simply Click to Change Your Location in Pokémon GO20 setembro 2024
Simply Click to Change Your Location in Pokémon GO20 setembro 2024 -
 Licensing20 setembro 2024
Licensing20 setembro 2024 -
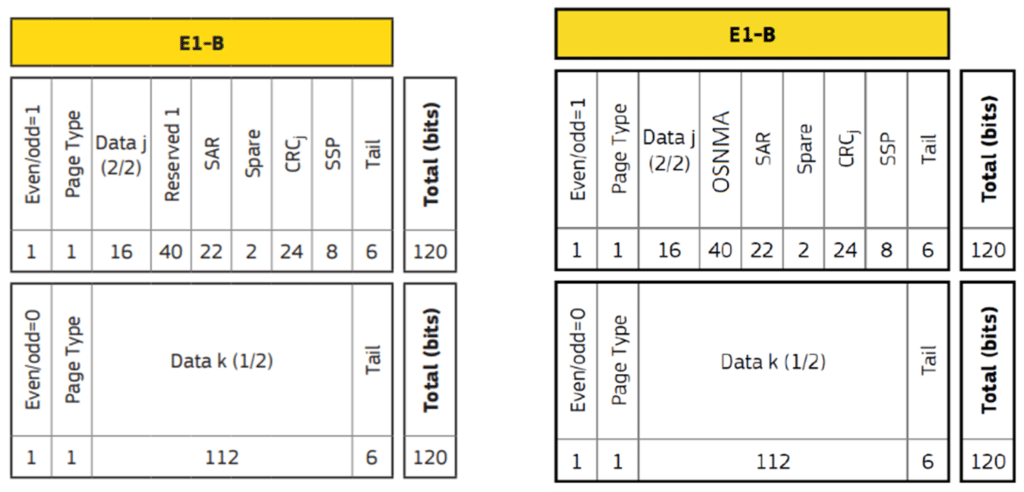 Testing a Receiver's Galileo OS-NMA Capability Using Skydel20 setembro 2024
Testing a Receiver's Galileo OS-NMA Capability Using Skydel20 setembro 2024 -
 1PC RED MAGIC Quasi-Speed Fan Simulator Spoofer Remover for20 setembro 2024
1PC RED MAGIC Quasi-Speed Fan Simulator Spoofer Remover for20 setembro 2024 -
 DeepPOSE: Detecting GPS spoofing attack via deep recurrent neural network - ScienceDirect20 setembro 2024
DeepPOSE: Detecting GPS spoofing attack via deep recurrent neural network - ScienceDirect20 setembro 2024
você pode gostar
-
 The King of Fighters 2002 Unlimited Match Kyo Kusanagi 1/12 Scale BBTS Exclusive Figure20 setembro 2024
The King of Fighters 2002 Unlimited Match Kyo Kusanagi 1/12 Scale BBTS Exclusive Figure20 setembro 2024 -
 House Head vs Siren Head. #shorts - Siren, Baby boy valentine pictures, Valentine picture20 setembro 2024
House Head vs Siren Head. #shorts - Siren, Baby boy valentine pictures, Valentine picture20 setembro 2024 -
 Anime Demônio Slayer Kimetsu Não Yaiba Kibutsuji Muzan Cosplay Traje Feminino Quimono Meninas Vestido De Halloween Preto Peruca Roupa - Trajes De Cosplay - AliExpress20 setembro 2024
Anime Demônio Slayer Kimetsu Não Yaiba Kibutsuji Muzan Cosplay Traje Feminino Quimono Meninas Vestido De Halloween Preto Peruca Roupa - Trajes De Cosplay - AliExpress20 setembro 2024 -
 The Wii U Laid The Groundwork For The Nintendo Switch20 setembro 2024
The Wii U Laid The Groundwork For The Nintendo Switch20 setembro 2024 -
Perguntas para Casal - Quiz APK (Android Game) - Free Download20 setembro 2024
-
 Old Sanrio Stores : r/nostalgia20 setembro 2024
Old Sanrio Stores : r/nostalgia20 setembro 2024 -
 Nezuko-chaaaan! : r/GachaClub20 setembro 2024
Nezuko-chaaaan! : r/GachaClub20 setembro 2024 -
 Brain Test Level 185 Best Solution Brain Test Solution Walkthrough20 setembro 2024
Brain Test Level 185 Best Solution Brain Test Solution Walkthrough20 setembro 2024 -
 Crash Team Rumble Game Review20 setembro 2024
Crash Team Rumble Game Review20 setembro 2024 -
 Boruto: Naruto the Movie's New Manga One-Shot Previewed - News - Anime News Network20 setembro 2024
Boruto: Naruto the Movie's New Manga One-Shot Previewed - News - Anime News Network20 setembro 2024
