Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Last updated 20 setembro 2024
Empty list for endpoint and domain nodes after agent deployment - OfficeScan
Requesting website reclassification
Evaluate Microsoft Exchange Online modules - Cloud App Security
Collecting debug logs - Portable Security 3.0
How to report misrated websites to Trend Micro
Feature testing steps - OfficeScan XG

What is EAP-TLS?
1 in Cloud Security & Endpoint Cybersecurity
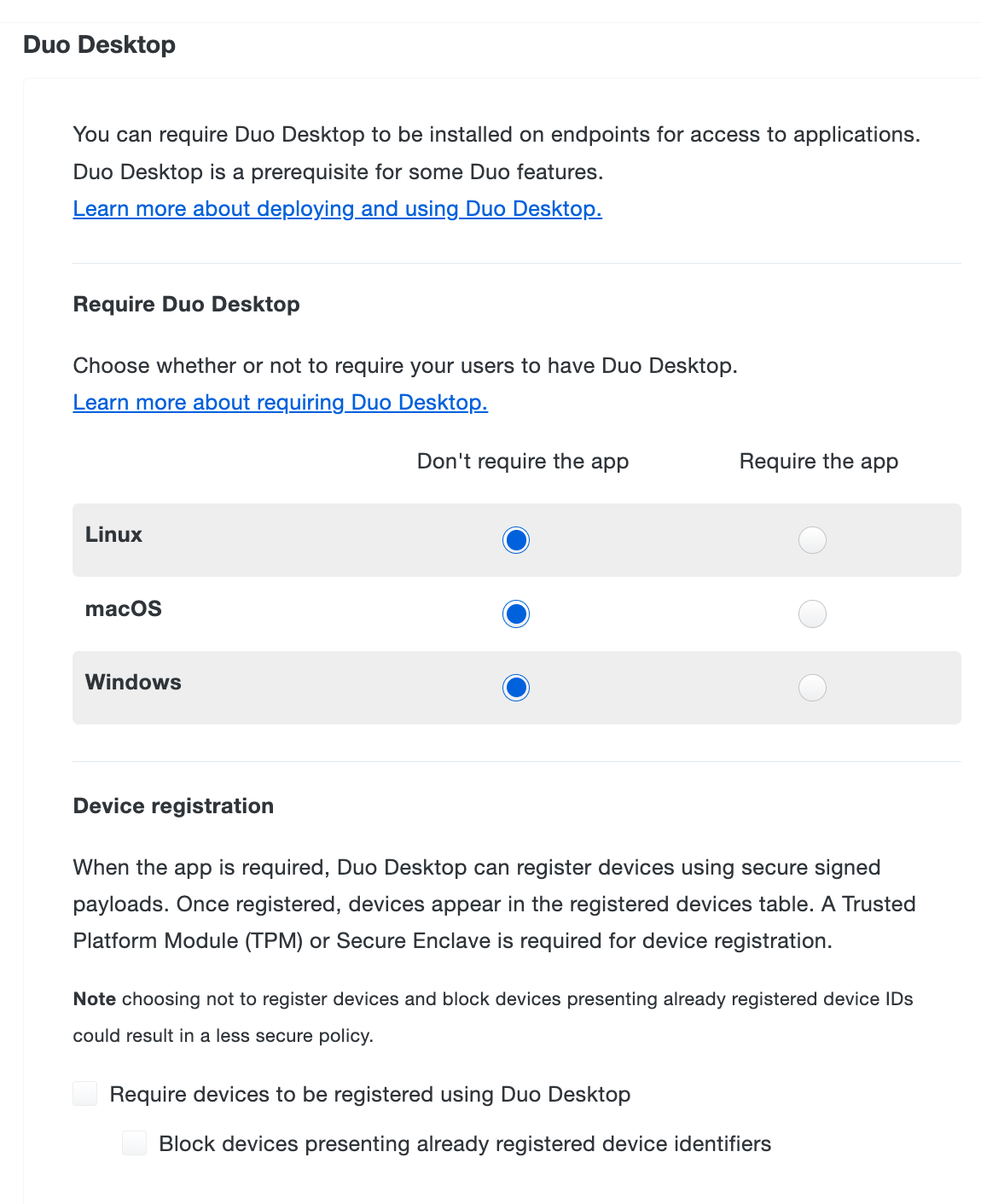
Duo Administration - Policy & Control
Known issues - Licensing Management Platform

Connected Philanthropy Podcast - Foundant Technologies
Scam Page error from Trend Micro Security
Recomendado para você
-
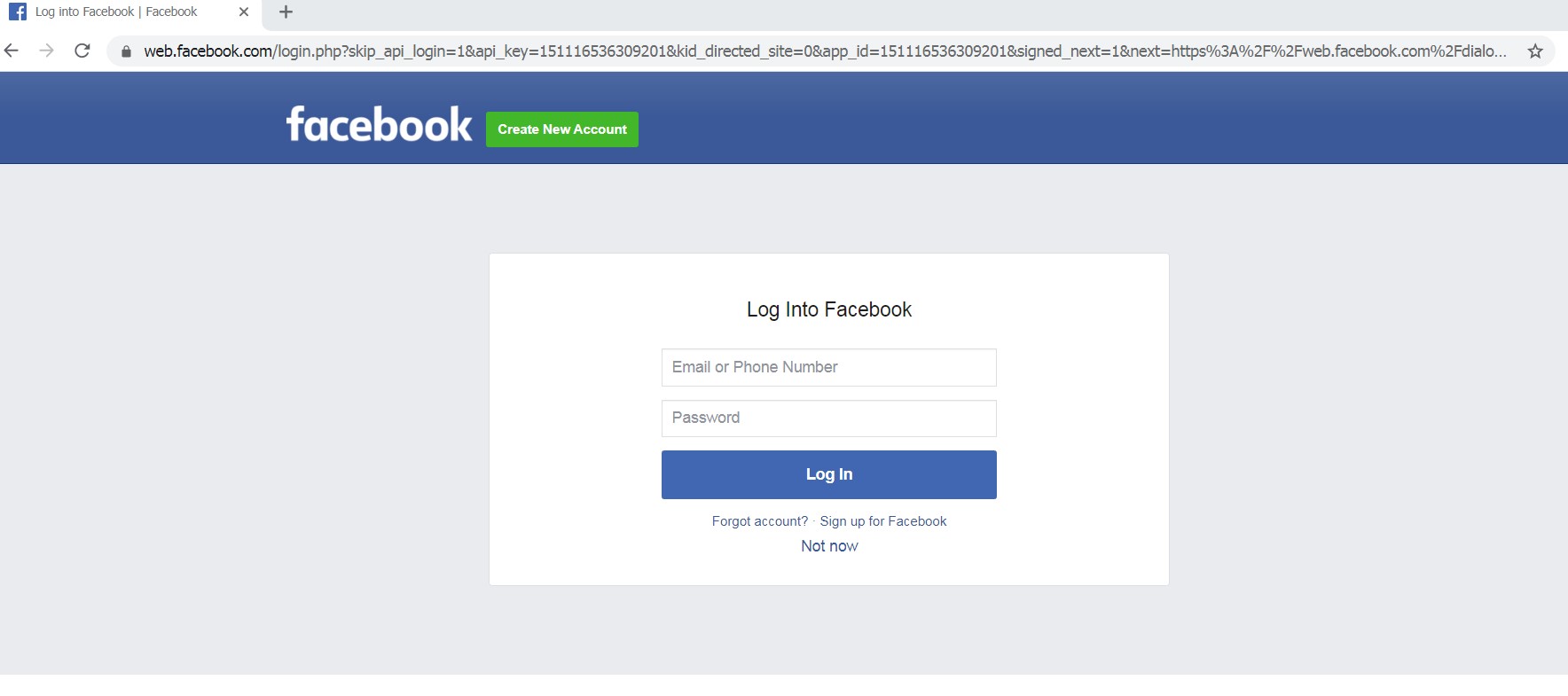
 Facebook Login20 setembro 2024
Facebook Login20 setembro 2024 -
 How to add Facebook App Login to Your WordPress Website - UsersWP20 setembro 2024
How to add Facebook App Login to Your WordPress Website - UsersWP20 setembro 2024 -
 Implement Facebook Login with PHP20 setembro 2024
Implement Facebook Login with PHP20 setembro 2024 -
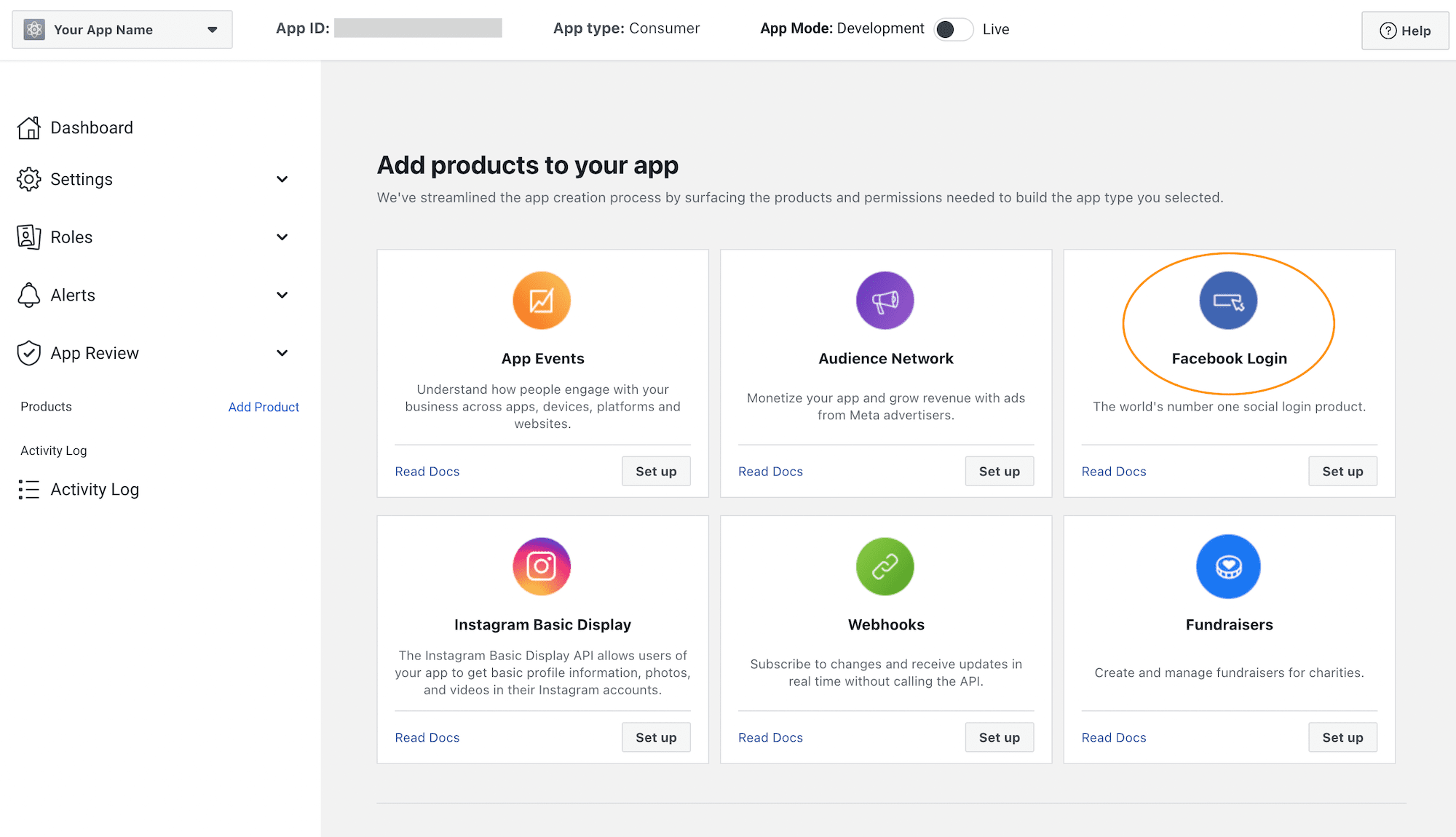 How To Add Facebook Login To Your Moodle 4.0+ Site - eLearning Themes20 setembro 2024
How To Add Facebook Login To Your Moodle 4.0+ Site - eLearning Themes20 setembro 2024 -
 Facebook taps FIDO U2F for stronger login security20 setembro 2024
Facebook taps FIDO U2F for stronger login security20 setembro 2024 -
 Day 2 - Exploring Forms in React with a Facebook login clone - DEV Community20 setembro 2024
Day 2 - Exploring Forms in React with a Facebook login clone - DEV Community20 setembro 2024 -
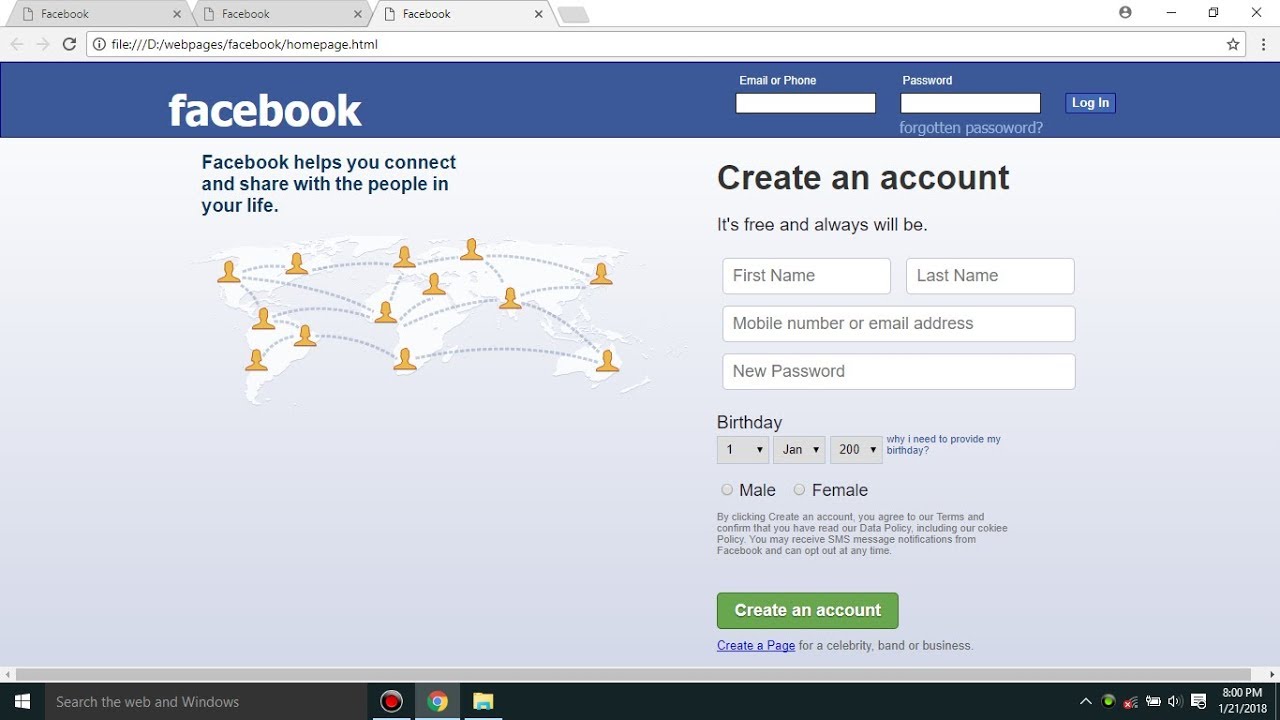 Facebook Login page Design, HTML, CSS20 setembro 2024
Facebook Login page Design, HTML, CSS20 setembro 2024 -
 Facebook Login20 setembro 2024
Facebook Login20 setembro 2024 -
 java - Require the user login facebook before he can use the App20 setembro 2024
java - Require the user login facebook before he can use the App20 setembro 2024 -
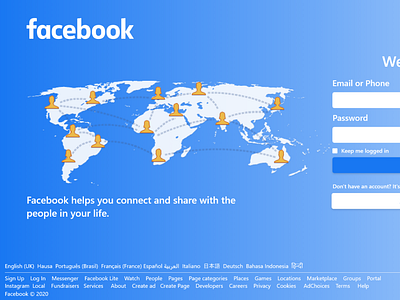 Facebook Login Page Design by Ifeoluwa Oyelakin on Dribbble20 setembro 2024
Facebook Login Page Design by Ifeoluwa Oyelakin on Dribbble20 setembro 2024
você pode gostar
-
:max_bytes(150000):strip_icc():focal(742x390:744x392)/Chrissy-Teigen-Instagram-tragus-ear-piercing-092823-9390c9bf889048c887ead23e627d5207.jpg) Chrissy Teigen Shares Image of Her Having New Tragus Ear Piercing20 setembro 2024
Chrissy Teigen Shares Image of Her Having New Tragus Ear Piercing20 setembro 2024 -
 City Background png download - 437*856 - Free Transparent Subway Surfers png Download. - CleanPNG / KissPNG20 setembro 2024
City Background png download - 437*856 - Free Transparent Subway Surfers png Download. - CleanPNG / KissPNG20 setembro 2024 -
![Monsters vs. Aliens [Blu-ray] [2009] - Best Buy](https://pisces.bbystatic.com/image2/BestBuy_US/images/products/9433/9433963_sa.jpg) Monsters vs. Aliens [Blu-ray] [2009] - Best Buy20 setembro 2024
Monsters vs. Aliens [Blu-ray] [2009] - Best Buy20 setembro 2024 -
 Jogar bem ou vencer?20 setembro 2024
Jogar bem ou vencer?20 setembro 2024 -
bucchigire #bucchigireanime #shineonbakumatsubadboys #akira #katsurak20 setembro 2024
-
 Resident Evil 3 Remake All In-Game Rewards DLC Coming In August, RE Resistance Getting RE2 Skins - PlayStation Universe20 setembro 2024
Resident Evil 3 Remake All In-Game Rewards DLC Coming In August, RE Resistance Getting RE2 Skins - PlayStation Universe20 setembro 2024 -
 Ben 10: Alien Force Season 1 Air Dates & Countdown20 setembro 2024
Ben 10: Alien Force Season 1 Air Dates & Countdown20 setembro 2024 -
 Tô Pouco Me Fodendo Em Ser um Santo, Sou Um Médico, Caralho20 setembro 2024
Tô Pouco Me Fodendo Em Ser um Santo, Sou Um Médico, Caralho20 setembro 2024 -
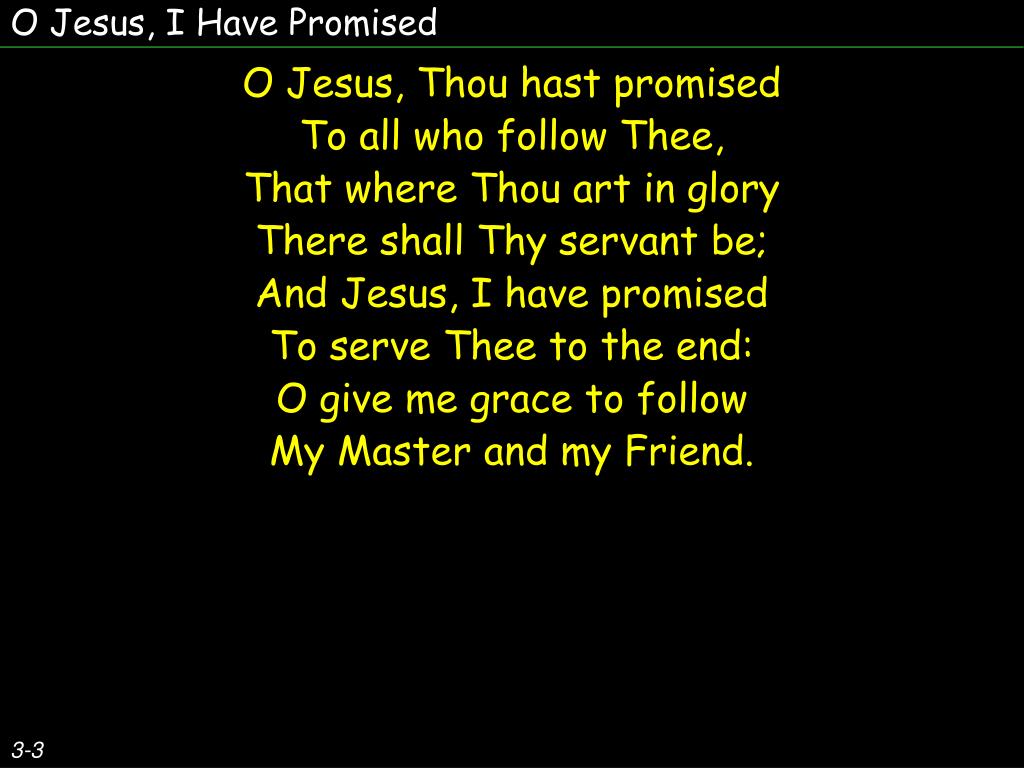 PPT - O Jesus, I Have Promised PowerPoint Presentation, free20 setembro 2024
PPT - O Jesus, I Have Promised PowerPoint Presentation, free20 setembro 2024 -
 Ave Mujica Alea jacta est First Limited Edition CD + Blu-ray20 setembro 2024
Ave Mujica Alea jacta est First Limited Edition CD + Blu-ray20 setembro 2024
